HIPAA Compliance – Securing Healthcare Data on Mobile Devices
Mai 11, 2017 | 42Gears Team
The influx of mobile devices in workspaces has changed the perception of governing bodies about healthcare data security policies. With the invention of mobile and internet technologies, the method of data transmission has evolved considerably. Mobile devices allow access to corporate data and applications from any part of the world via Cloud services and remote mobile desktops. As more sensitive information is being accessed through mobile applications and the network cloud in the healthcare industry, it is vital to ensure complete security, privacy and regulated compliance of information exchanged. The HIPAA (Health Insurance Portability and Accountability Act) in correlation with PHI (Protected Health Information) ensures healthcare organizations are held accountable for securing sensitive patient and business data during transmission or when it is stored on a mobile device.
A few months ago, a US hospital was required to pay a $3.2m fine due to HIPAA non-compliance after the loss of a healthcare device was found to have breached its protocols. As per the latest HIPAA report, 2016 was one of the worst years for healthcare data breaches. The total healthcare data breaches of 2016 were 16,471,765 records.
(Source: https://www.hipaajournal.com/hipaa-compliance-checklist/)
Since the introduction of the HIPAA breach notification rule in 2009, the U.S. Department of Health and Human Services (HHS) has reported 800+ breaches on its “wall of shame”. The rule requires organizations to report patient data breaches and was implemented to help healthcare organizations recognize the most common mistakes that cause data breaches. But this rule can also inadvertently damage the public image of a healthcare unit, leading to huge penalty fines. In 2016, $23.5 million were paid as 13 HIPAA enforcement fines. In most cases, the loss or theft of an official device was the leading cause of data breach.
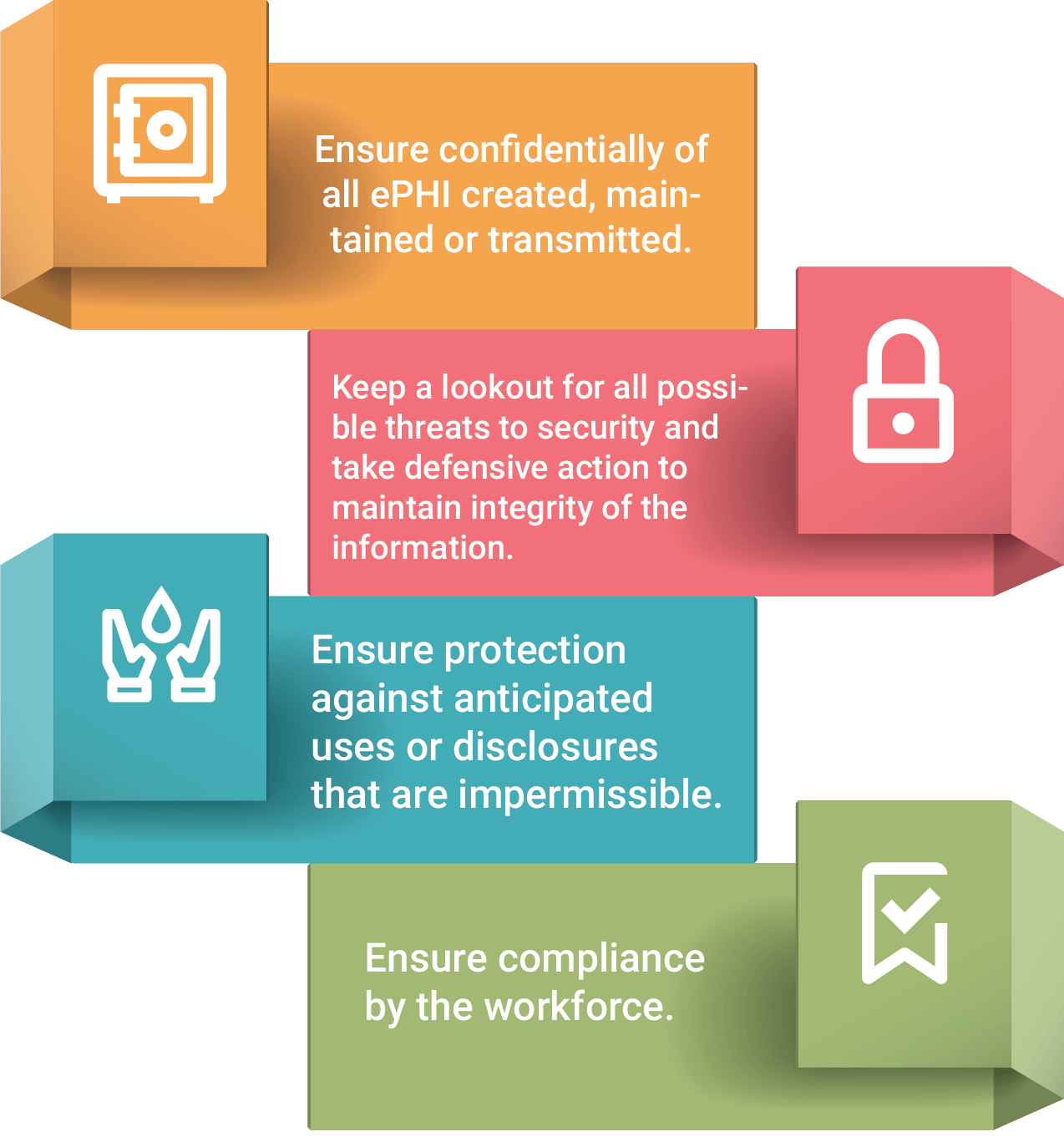
Hospitals have become stricter and more proactive in regulating their IT practices. The responsibility to identify the risk of breach and prevent data leaks before they occur is increasingly falling on healthcare IT departments. There is a need for healthcare organizations to adopt stringent security measures as per the privacy and security recommendations of HIPAA Security Rule.
The rule states the following steps are to be taken to comply with the recommendations:
Healthcare organizations have to analyze risks and identify potential points where data breach may occur on mobile devices to take preventive action and meet the requirements of the HIPAA Security Rule. It is necessary to have some basic security measures in place such as installing and enabling encryption to secure mobile devices that handle Electronic Protected Health Information (ePHI). Some of the key evaluation criteria on regulations and security considerations in healthcare sector need to be addressed while implementing mobility solutions.
In order to analyze risks of data breach through mobile devices, healthcare organizations will have to establish how ePHI is used on mobile devices. It is necessary to ascertain the ways in which users access, stock or transmit ePHI on their mobile devices. Healthcare organizations have to learn to identify risk areas, which may differ from case to case. According to HIPPA Journal, the top five reasons for healthcare data breaches in 2016 were unauthorized access/disclosure, hacking/IT incident, theft, loss and improper disposal of mobile devices.
42Gears EMM solutions help protect data at every stage.
As per HHS’s endorsements for securing ePHI on mobile devices used by healthcare organizations, the following steps are to be undertaken to remain HIPAA compliant and protect patient information:
Input a Password Credential
According to HHS, using a strong password is one of the most vital steps. Users are recommended to keep a password that is at least six characters in length and features a combination of upper and lower case letters, a special character and a number. SureMDM utilizes ‘Profiles’ section to enforce passcode policies on devices. IT admins will have the ability to set complex passcodes, define the minimum character length, set the maximum failed attempts, the maximum time to lock and maximum password age.
Encryption Protection
As per HHS recommendation, data stored or exchanged by mobile devices has to be protected with government-grade FIPS 140-2 encryption. 42Gears applies security and containerization techniques to protect data stored or exchanged through enterprise applications. Administrators are also offered the ability to make use of native encryption features that come built into the device OS. Encryption is offered at various levels – data at rest and data over the air to prevent copy/paste and opening files in other applications.
Remote Wiping and/or Disabling
42Gears allows admin to install and activate remote wiping and/or remote disabling to comply with HHS recommends. The IT admin of an organization can remotely disable access and wipe data in the case of loss or theft of a device. If an employee leaves the organization, IT administrators can activate an enterprise-level or device-level wipe action remotely from the central console.
Restrict File Sharing Applications
HHS recommends preventing file sharing applications from being used on enterprise devices. It is likely that some users would have consumer file share services installed on their devices. To ensure that data and documents stored in these services are not misused, our EMM solution creates a separate work container on employee’s personal devices. The container would prevent file sync and file share to occur with employee’s personal content. The container allows administrators to manage and control access to official content across all devices from a central console.
Keep Security Software up to Date
As per HHS recommendations, it is vital to enable security software on mobile devices and keep it up to date. By using our enterprise-grade solutions, IT administrator will be able to maintain an oversight of all devices with access to sensitive information. IT admins can push software updates or prompt users to make updates and monitor compliance.
Stay Connected with Devices
HHS asks healthcare organizations to ensure that its employees maintain physical control of their enterprise-use devices at all times. With SureMDM console, IT admins will be able to get a real-time and comprehensive view of all their managed devices. They will get to see a high-level graphical view of the devices deployed, the full list of enrolled devices and also device and user information details. Administrators will have the ability to track the actual location of devices and take appropriate action if/when a risk is detected. In case of any compromise on the user’s physical control over the device, the admin can remotely lock or wipe the device data.
Exchange Health Information Over Secure Wi-Fi Networks
It is considered a best practice for healthcare facilities to send and receive patient information over a secure network. By using our EMM solution, administrators can limit the Wi-Fi connectivity for managed devices to a secure network, ensuring that devices with ePHI access won’t be able to access any public Wi-Fi network.
Wiping All Patient Information from Discarded Device
Once an enterprise use device is no longer used or becomes outdated, it is necessary to wipe all sensitive patient healthcare data before the device is discarded. With the help of SureMDM, the admin can perform a full device swipe on an enterprise-owned device, restoring it to its factory reset settings.
Healthcare is one of the most highly regulated industries and organizations operating in this sector must maintain compliance for all enterprise-use devices. This can be made easy with an Enterprise Mobility Management (EMM) program in place. With 42Gears EMM solution, organizations have the ability to collect and analyze data that is solely driven by the devices used for enterprise use. The SureMDM console’s dashboard will offer an overview of device deployment at any time and give details such as OS versions, device model names, device ownership and a list of devices not under compliance. Administrators can create custom reports showing info on content and application use, enrollment status and more.
With the help of 42Gears EMM product suite, healthcare organizations can help identify points of weakness in mobile security and ensure users are complying with rules for securing enterprise-use mobile devices.
Disclaimer: 42Gears does not claim that the organisations using our products/services will be HIPAA/GDPR/CCPA or any applicable regulations compliant or exempt from any legal or regulatory provision applicable thereto. Using the products/services will only assist customers in achieving certain mandates devised for the companies handling personal information of the end users.
Subscribe for our free newsletter