MTD - Mobile Threat Defense Solution
Identify and eliminate security vulnerabilities
Overview
64% of mobile threats come from your apps, and that's not all– leakware is present in 35% of all installed applications. If you are looking to proactively safeguard your endpoints and business data from cyber threats, deploying an MTD (Mobile Threat Defense) solution can help!
MTD solutions strengthen mobile security by preventing, detecting, and remediating sophisticated cyberattacks using advanced techniques. When integrated with a UEM platform, this powerful combination ensures comprehensive security management and robust policy enforcement.
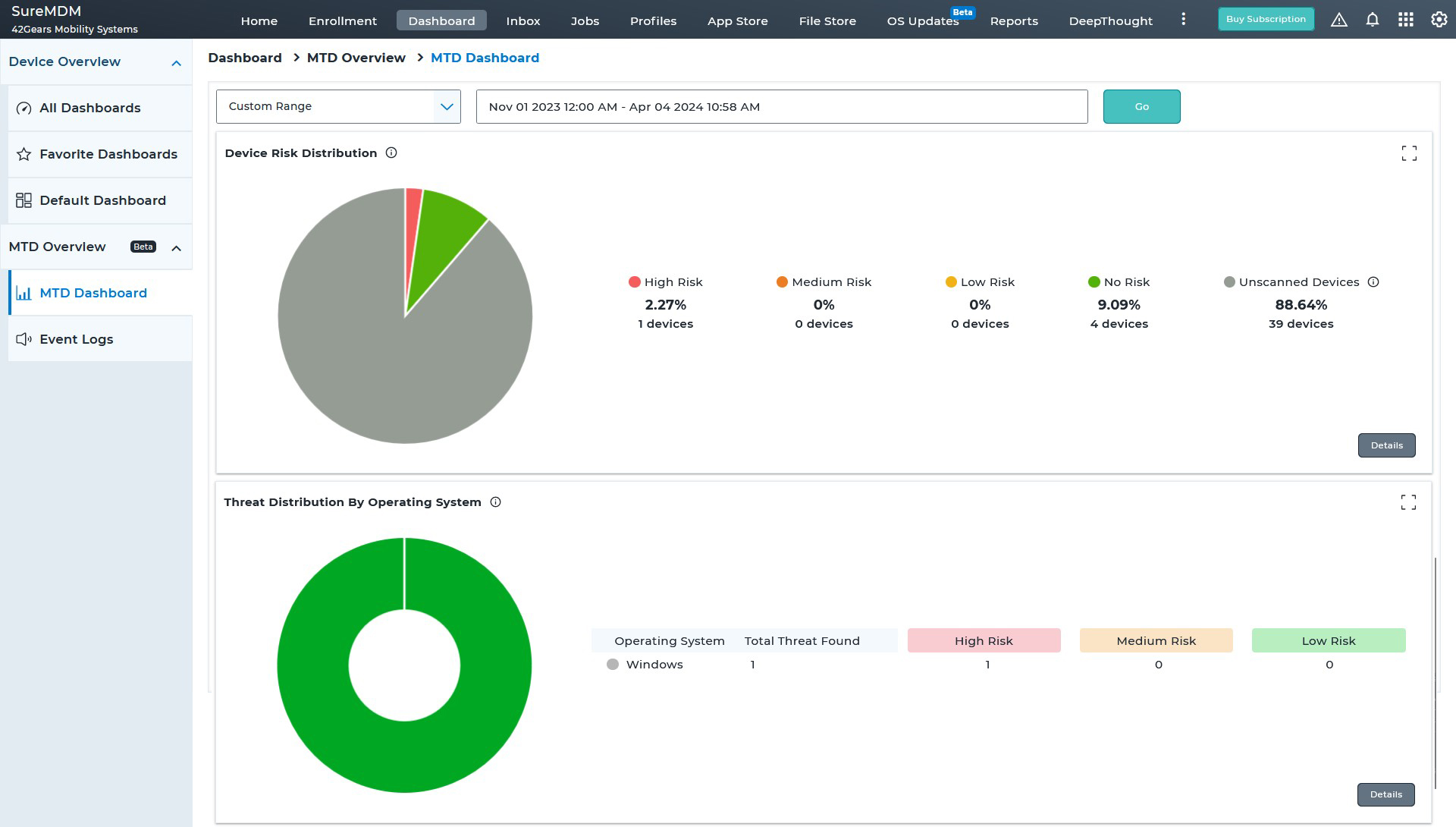
SureMDM seamlessly integrates with Pradeo, a leader in Mobile Security, to provide an MTD solution for securing and managing Android devices. With this integration, SureMDM now offers advanced mobile security capabilities to its users, allowing them to both manage and protect their mobile environment from a centralized SureMDM console.
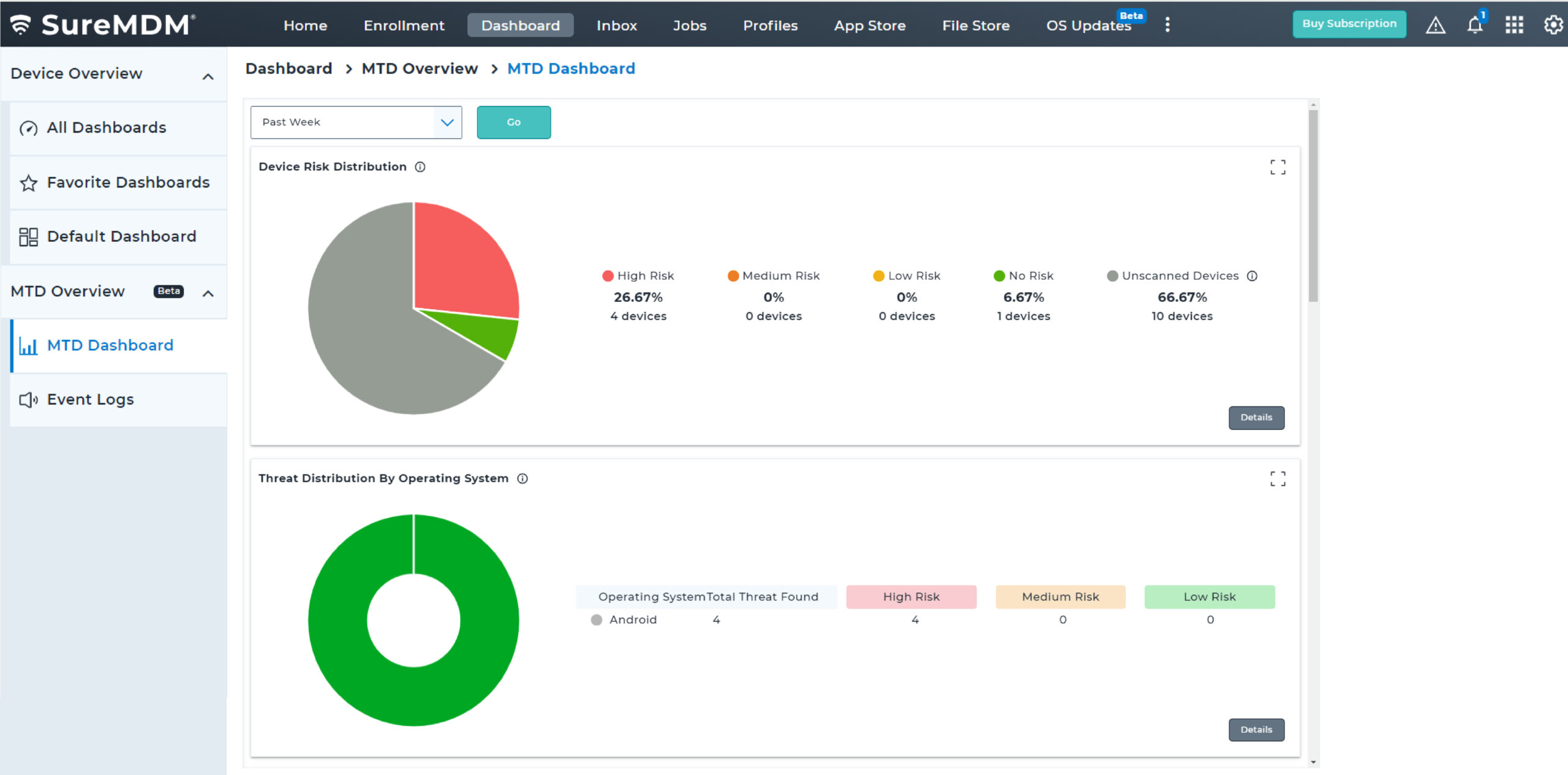
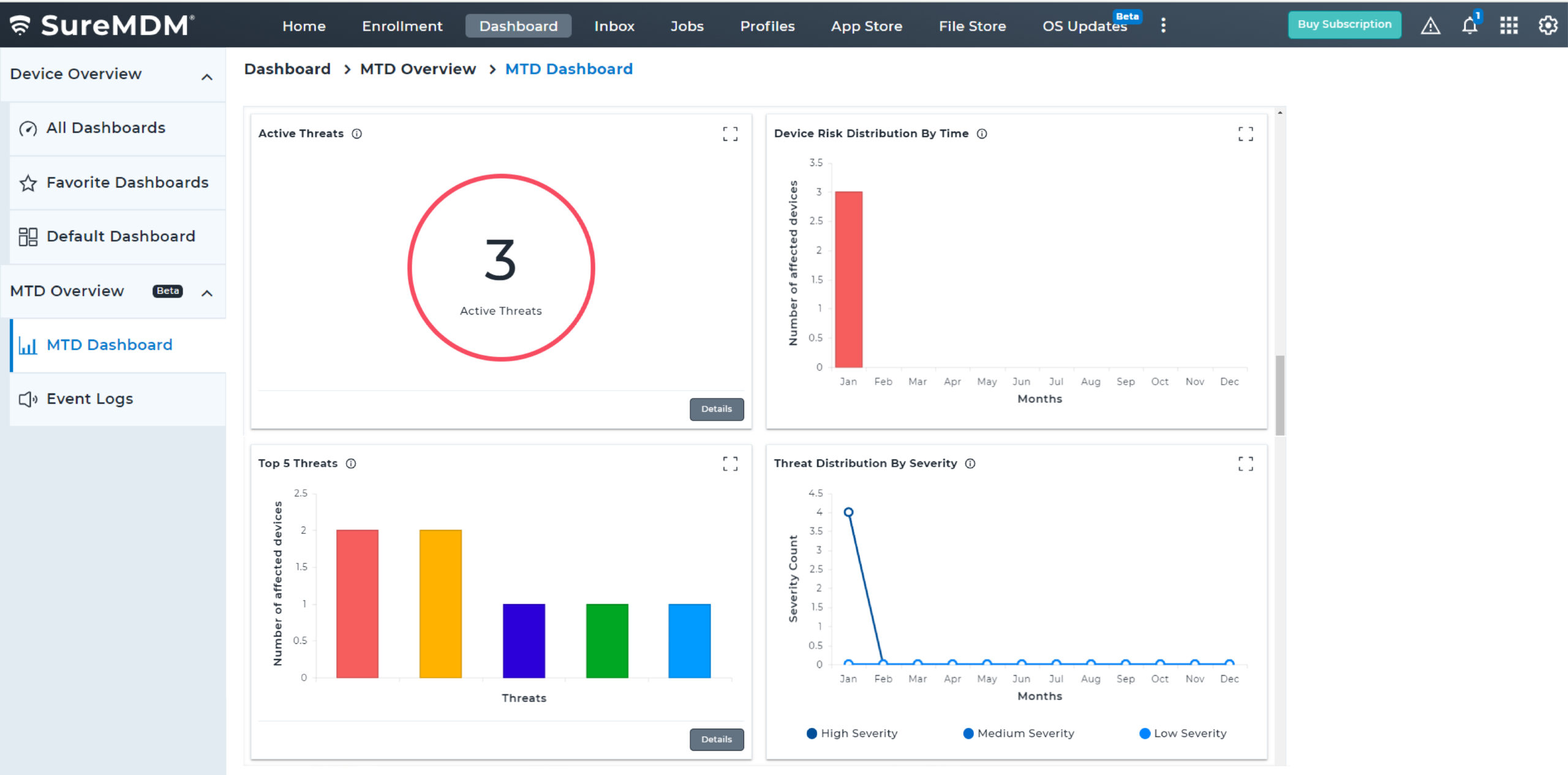
Threat Vectors that SureMDM MTD Android Solution Covers

Malware
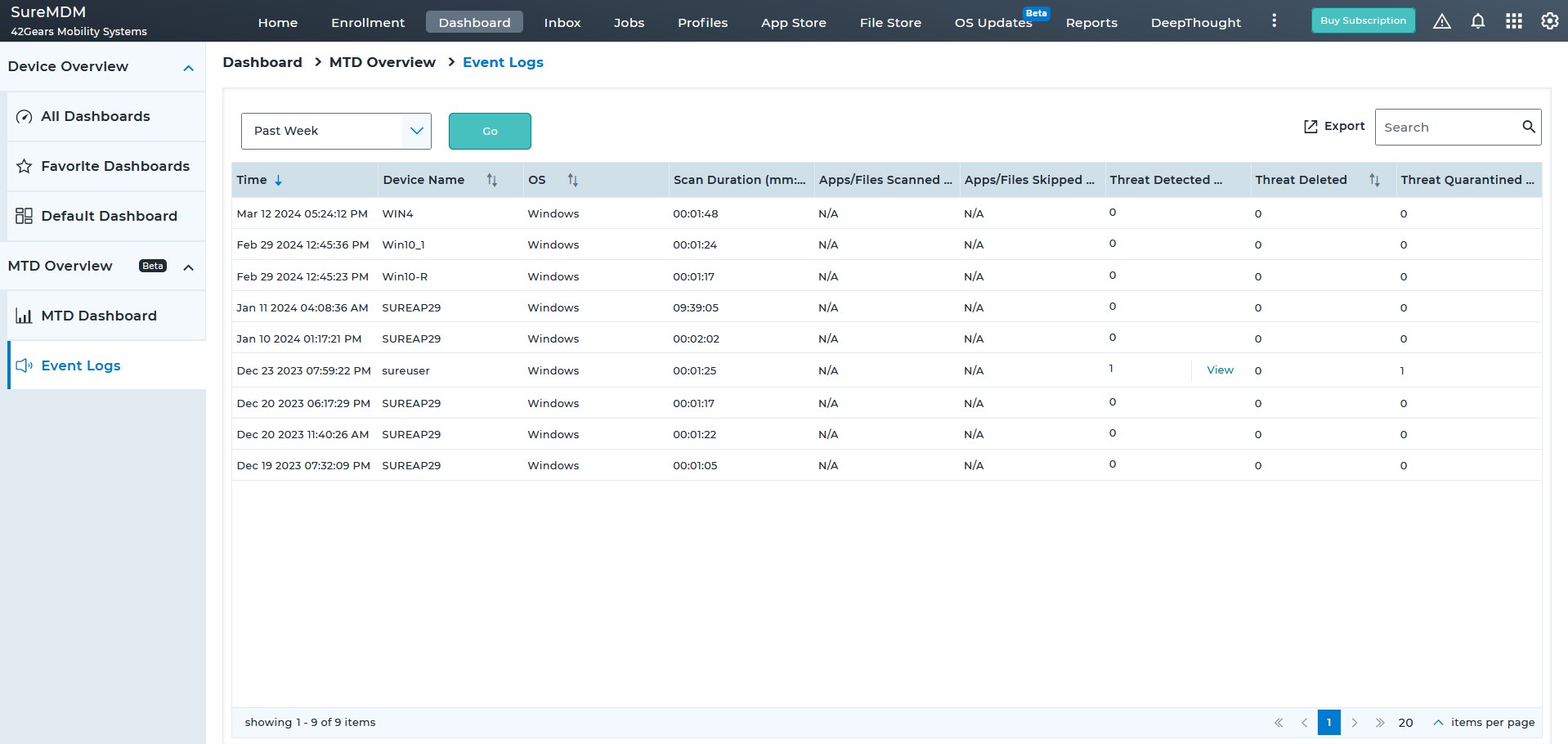
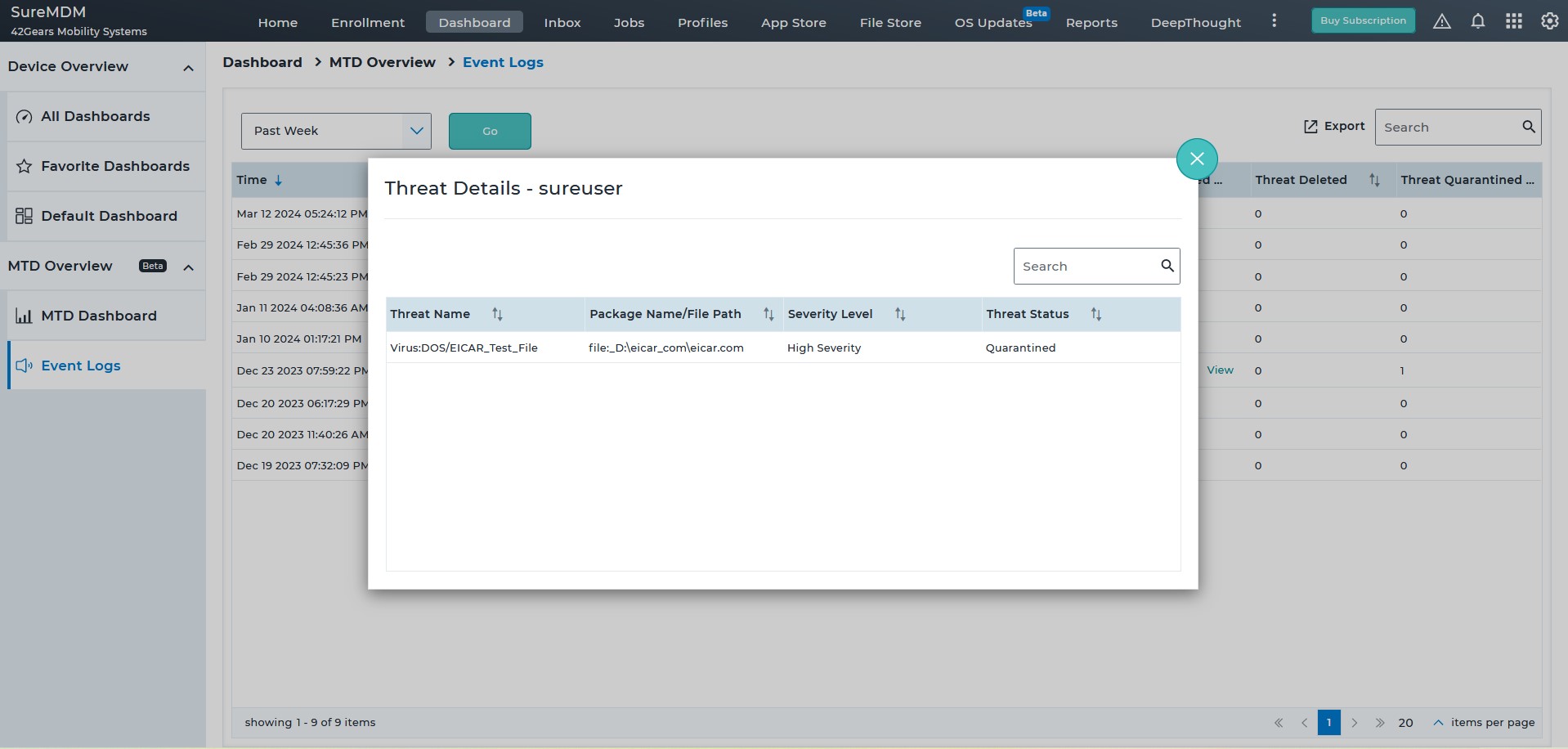
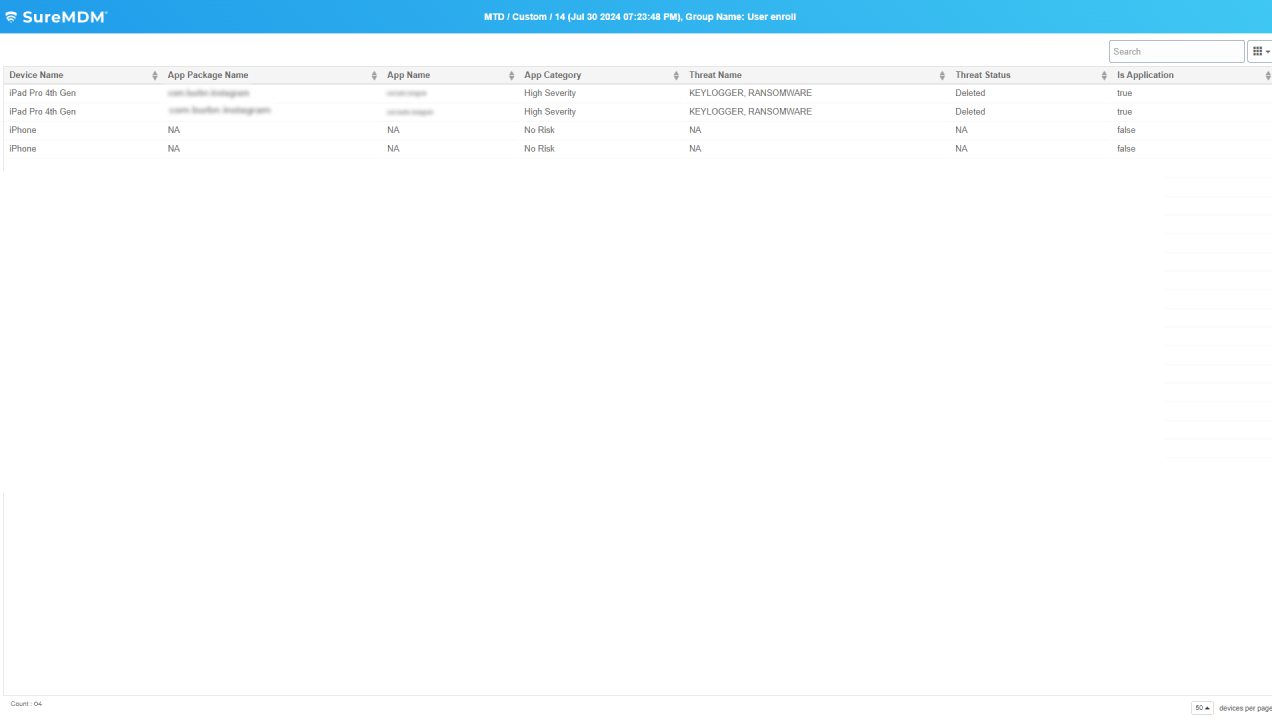
A malware is a malicious software that is intentionally designed by hackers for illegal activities such as eavesdropping or collecting passwords. Cybercriminals use mobile malware to lock devices and demand payment to return the data to users or unlock the device. The SureMDM Mobile Threat Defense solution can scan endpoints to monitor threats coming from all threat vectors, and then proactively remove the threats upon detecting irregular behavior.

Malicious Apps
Malicious apps are fake, unknown or dead apps that are repacked and laced with malicious codes. Users who install applications from third-party app stores may accidentally download malicious apps. SureMDM protects enterprise data by scanning and analyzing installed apps.
Key Features
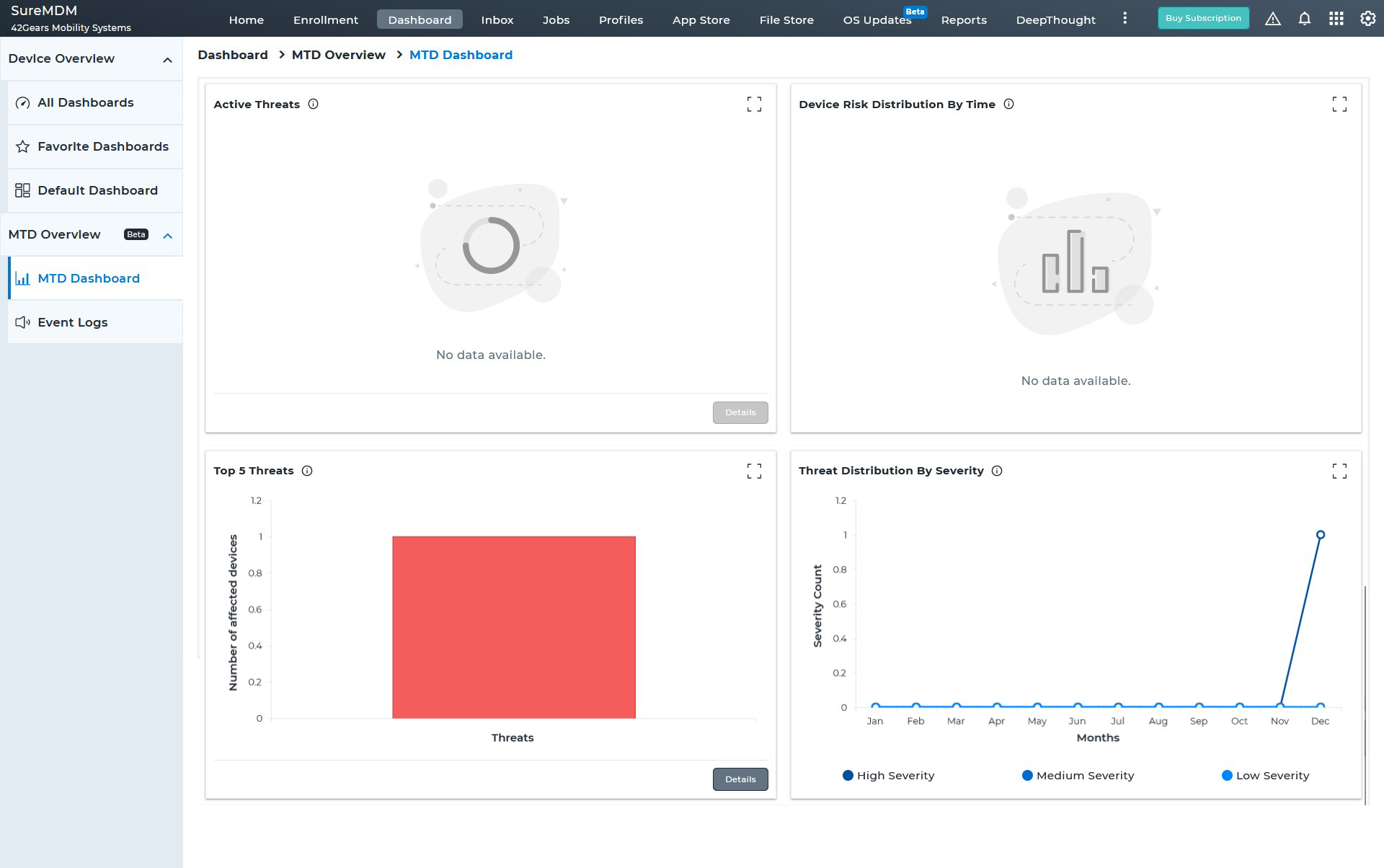
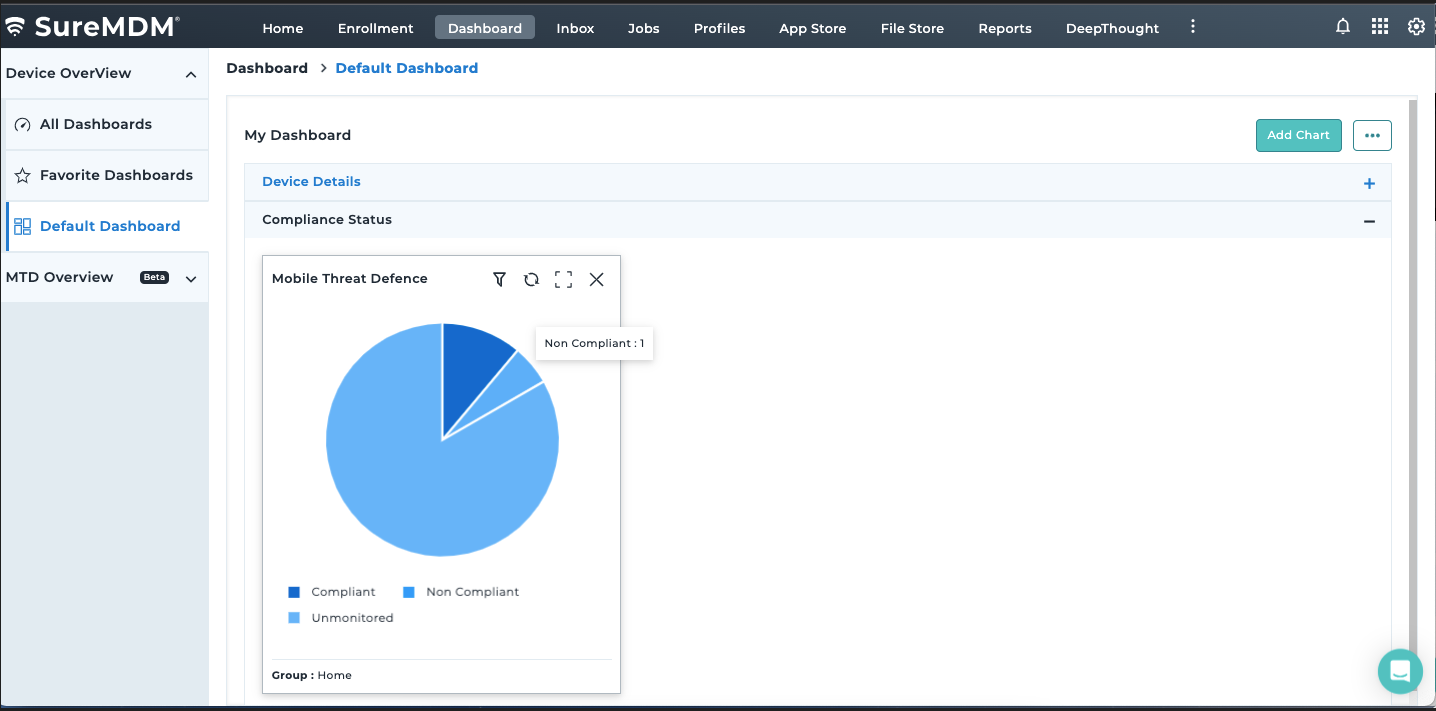
Proactively monitor the security of critical business applications by initiating continuous scans when devices are online. Choose between basic scan and full device scans to meet different requirements.
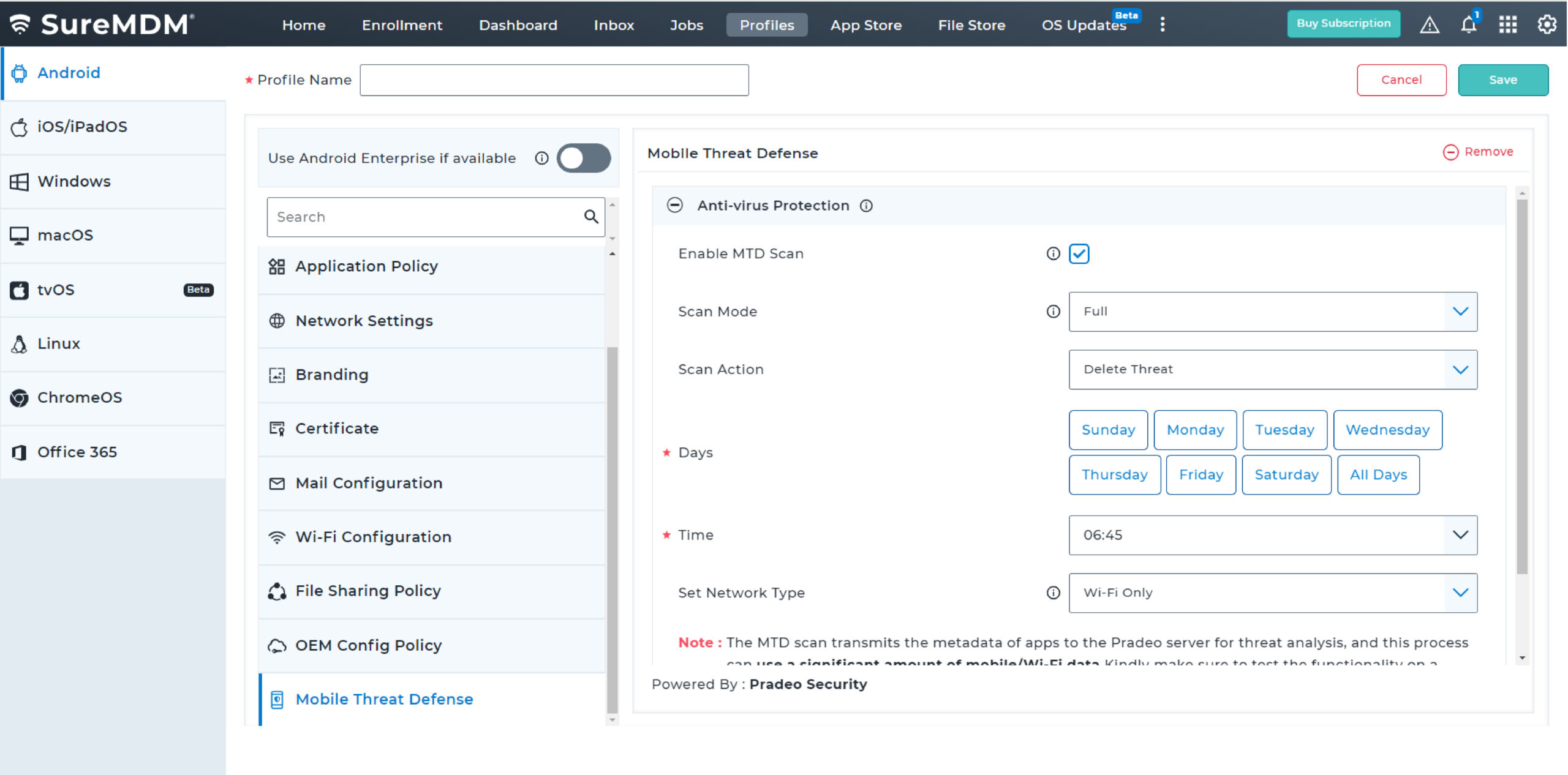
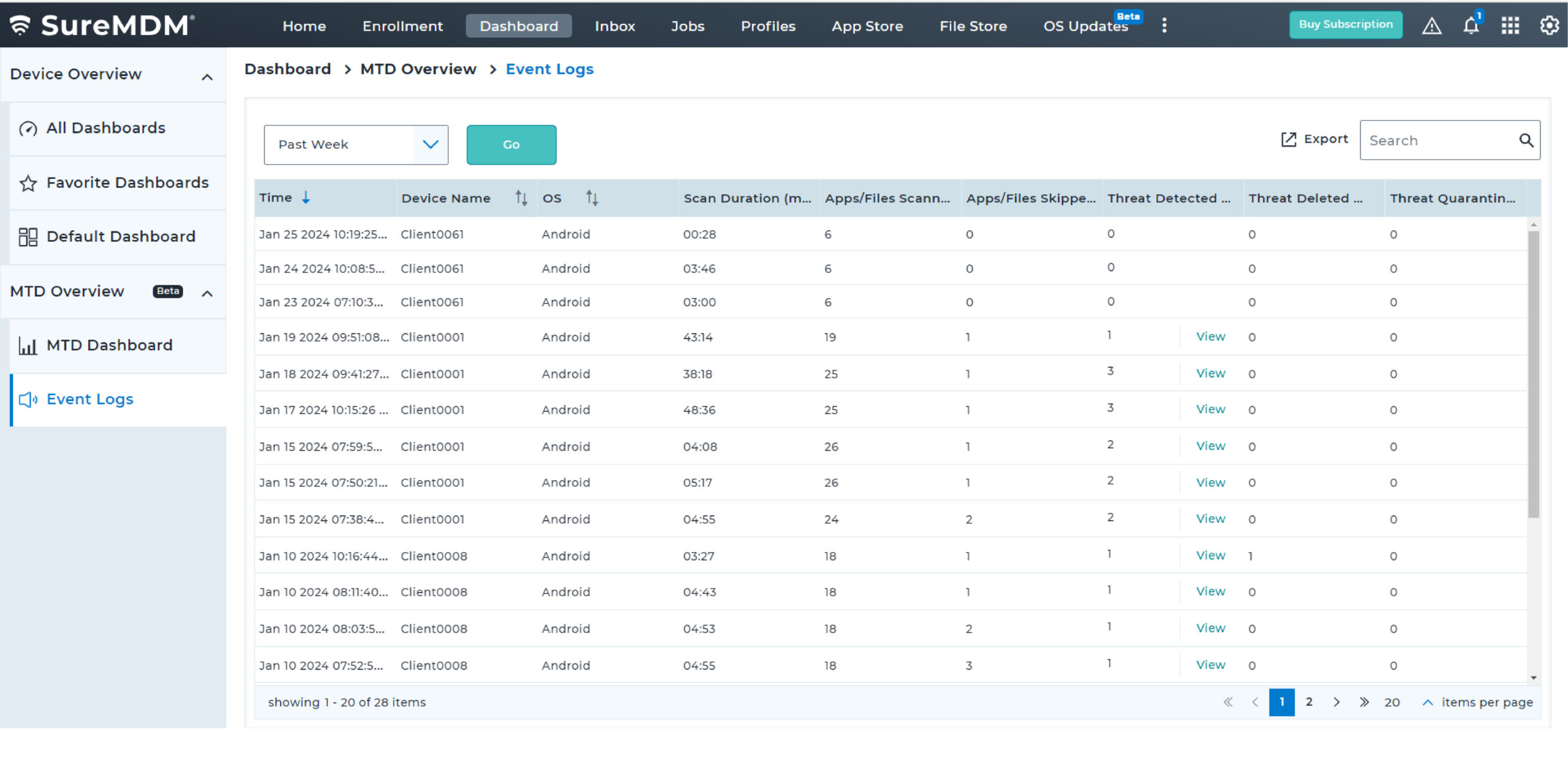
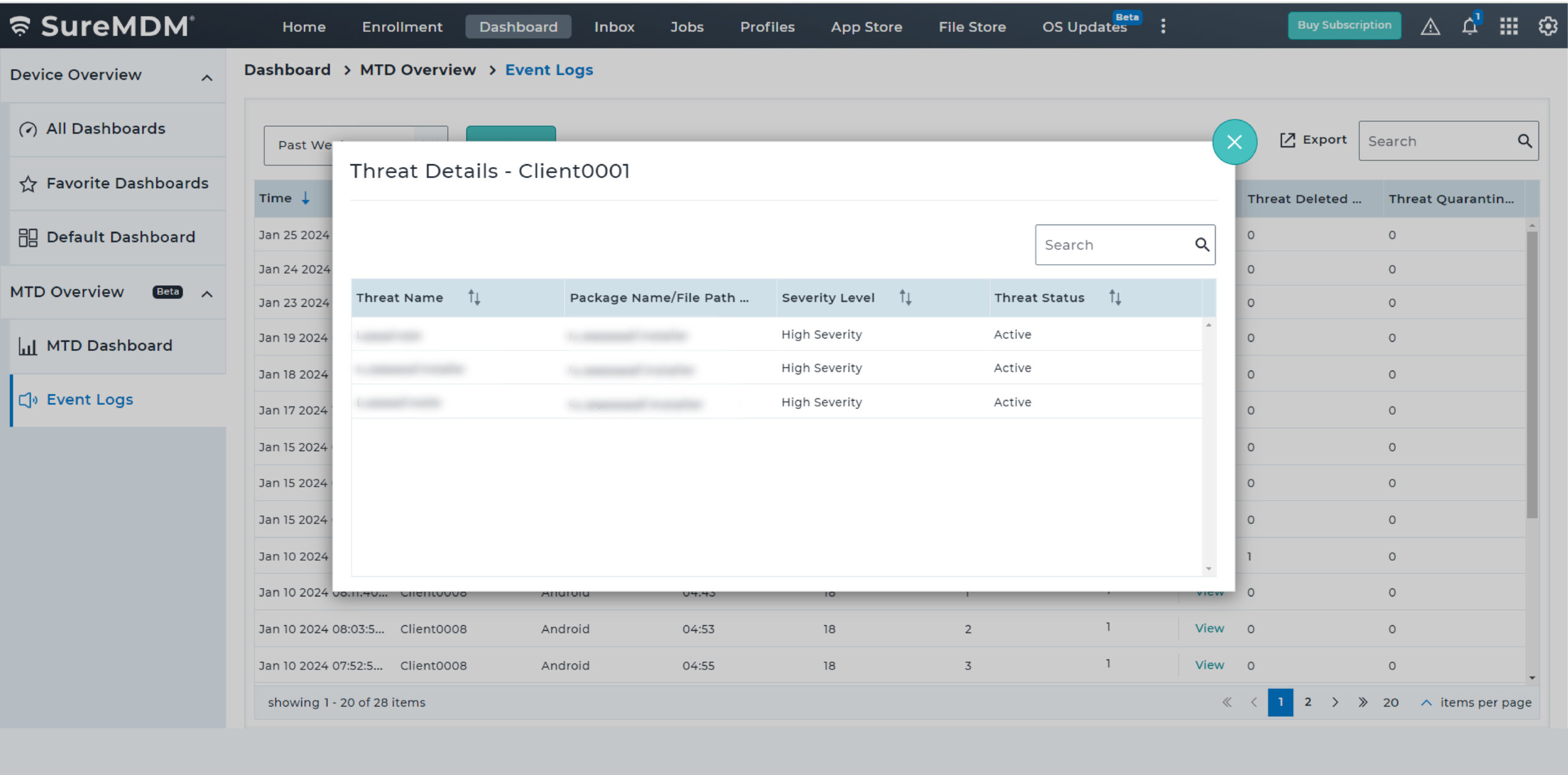
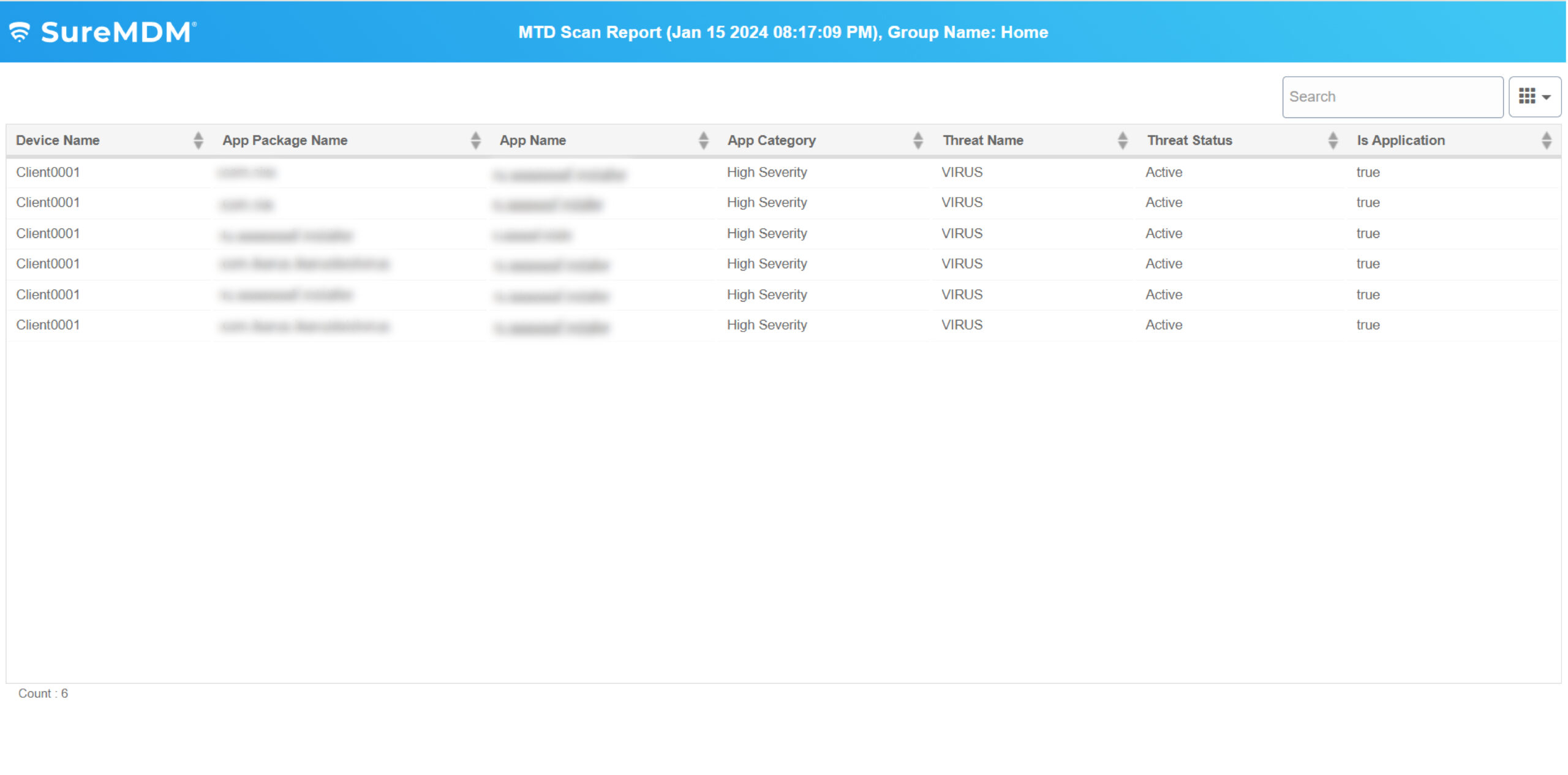
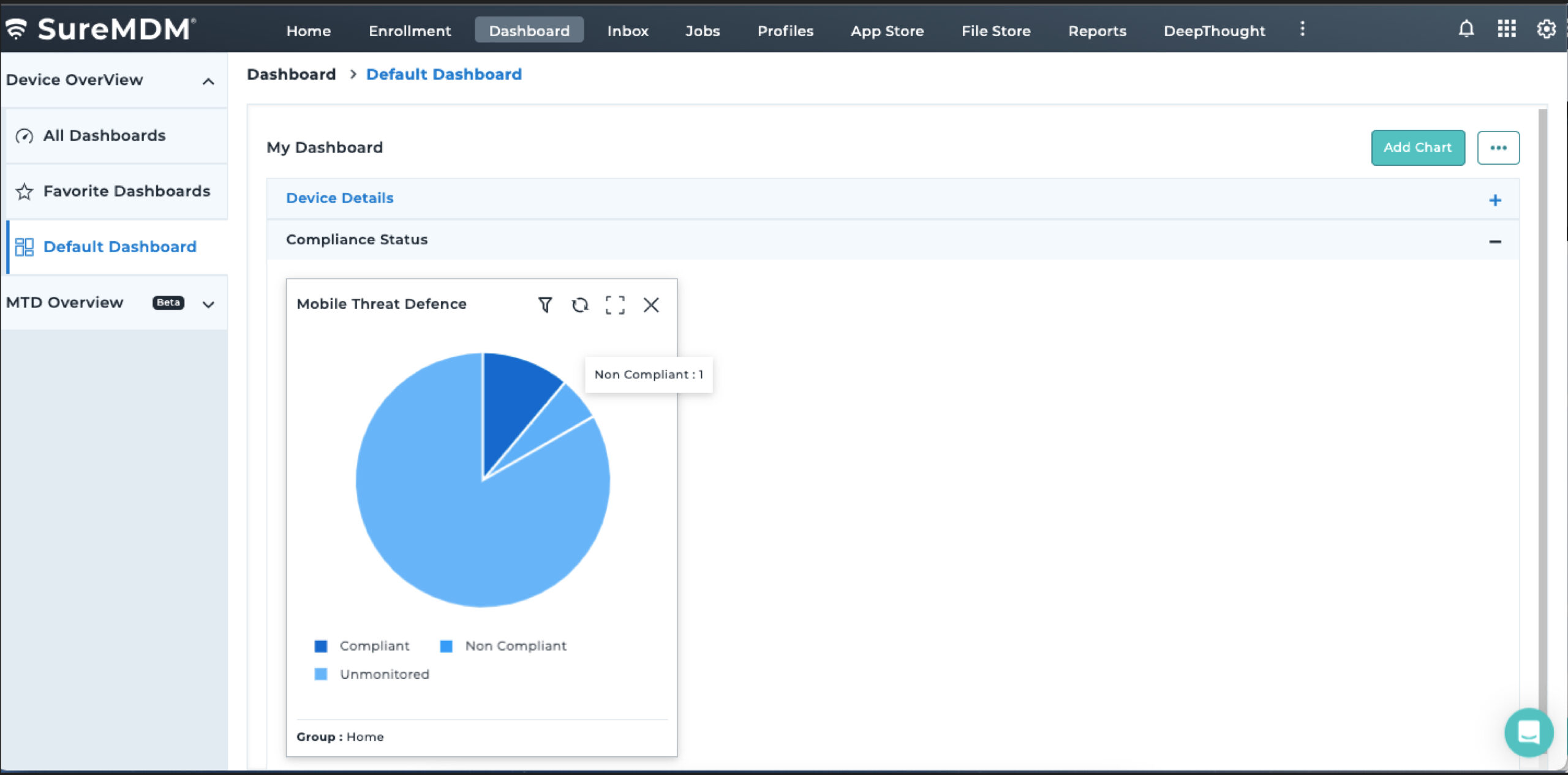
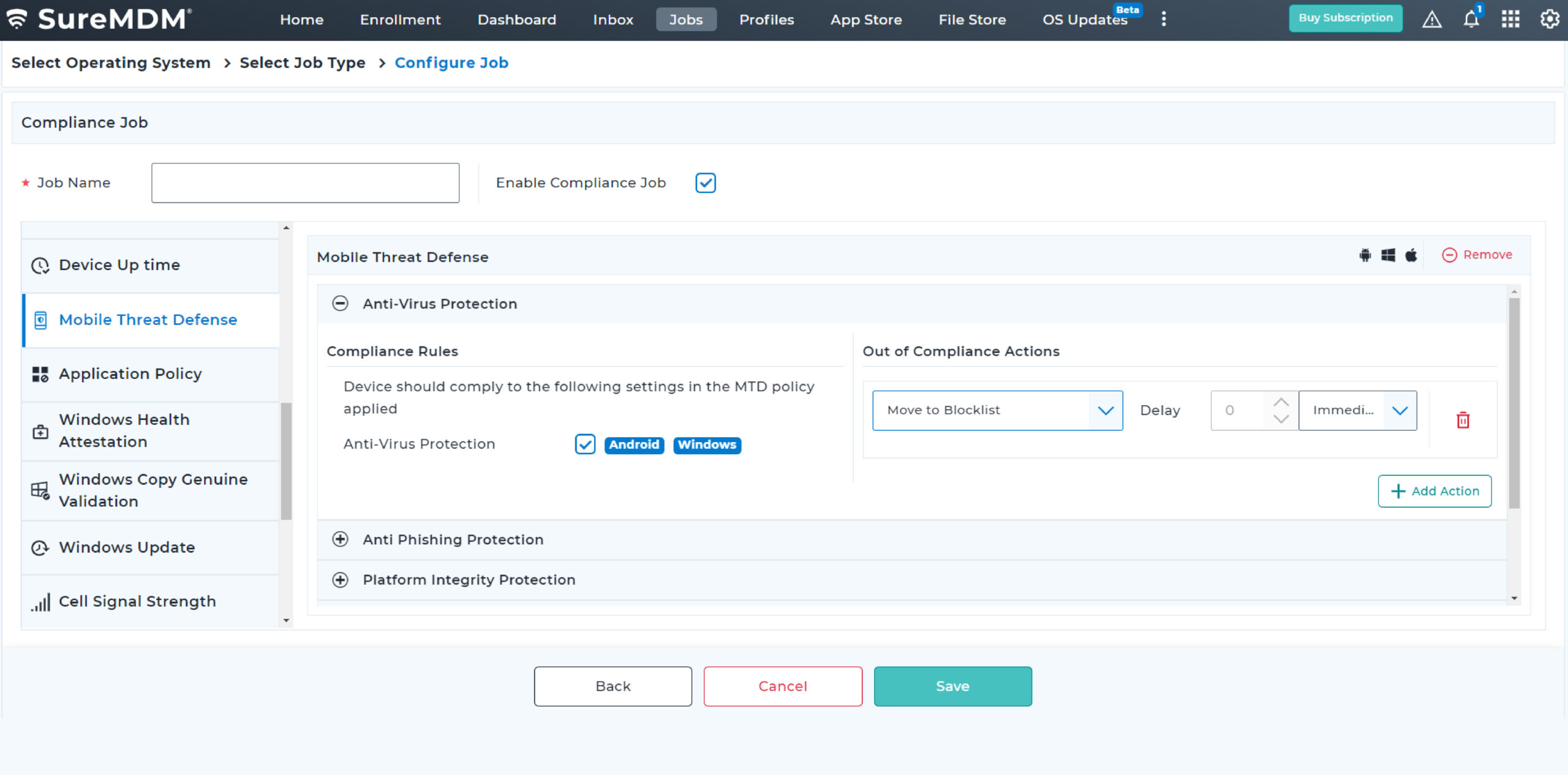
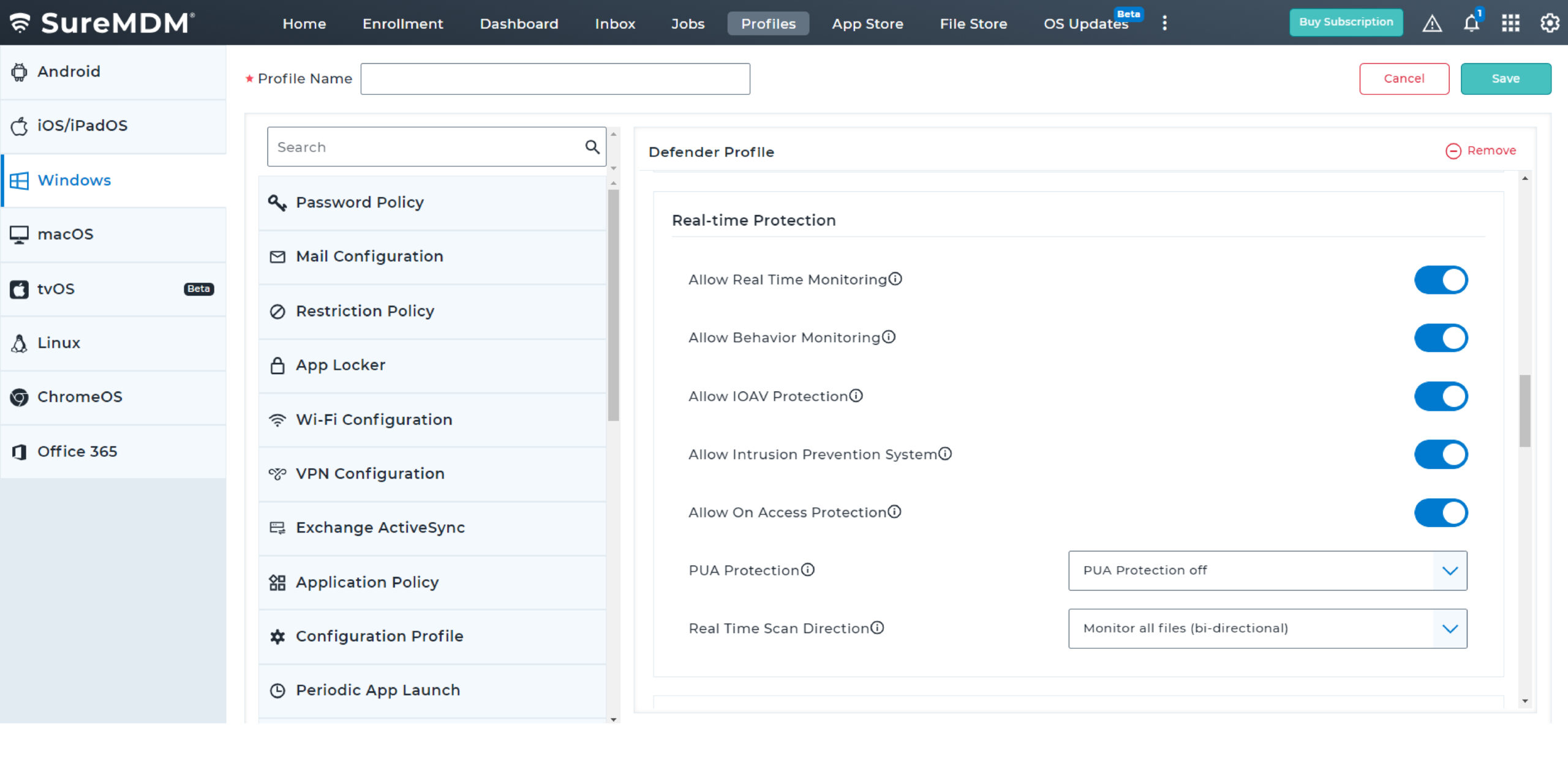
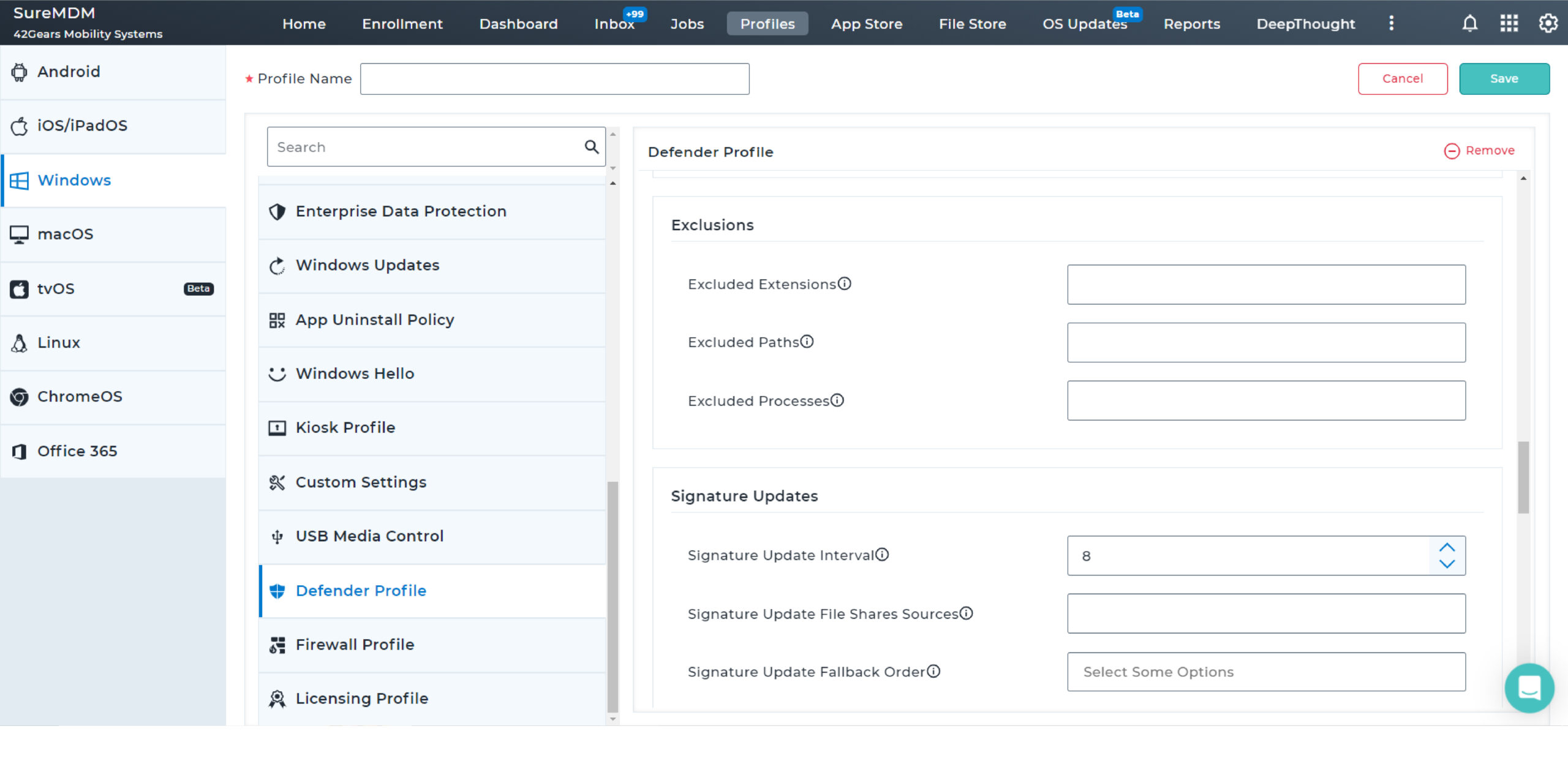
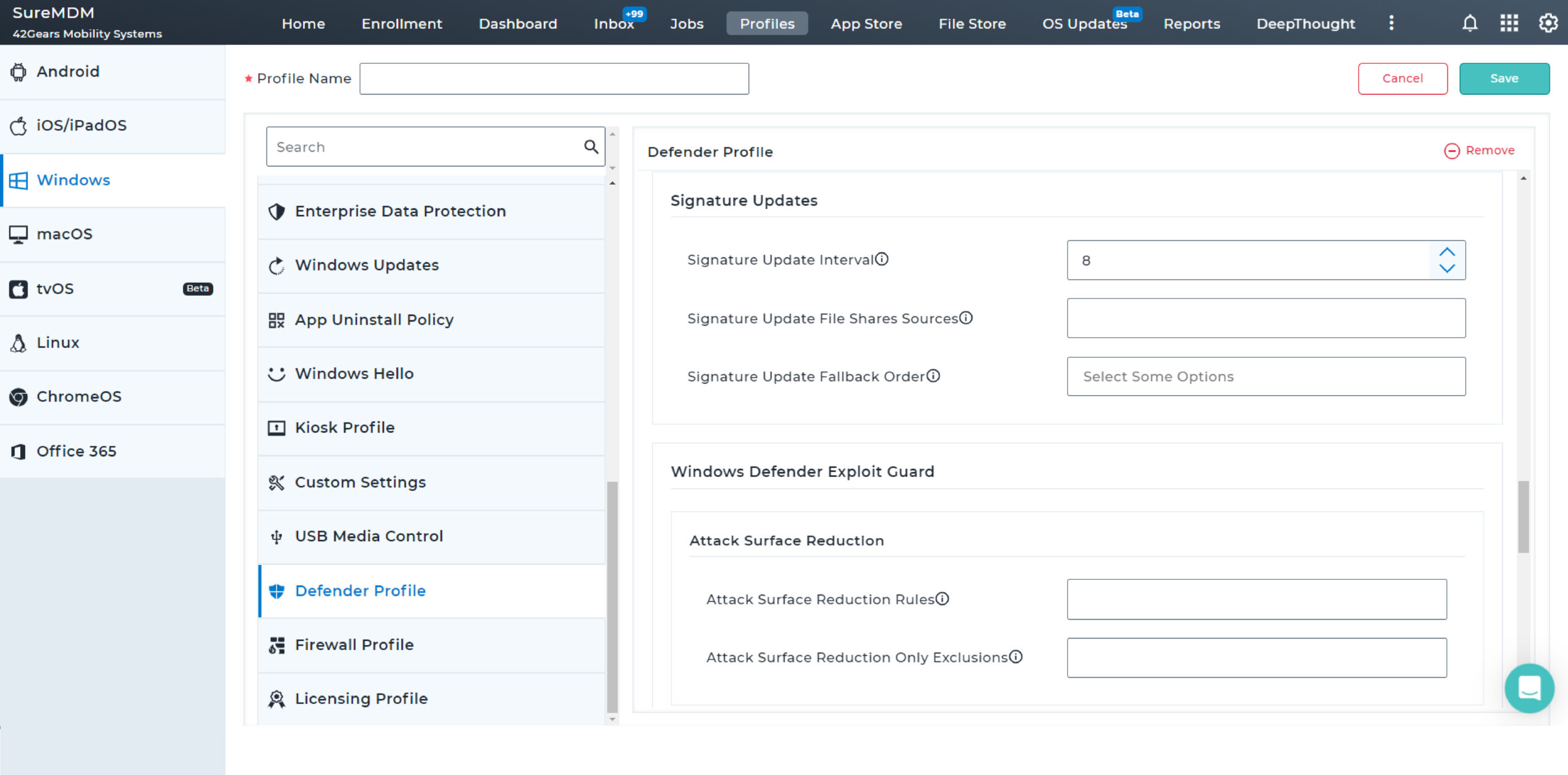
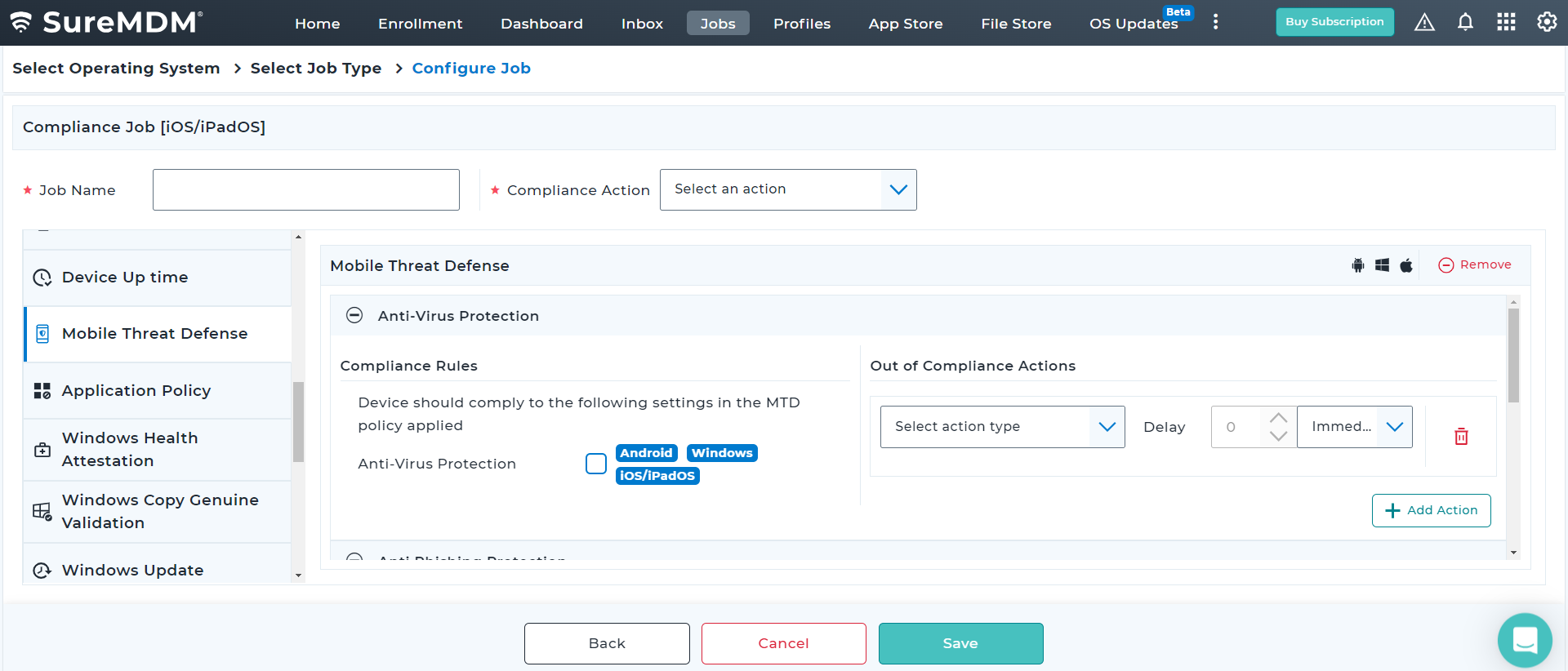
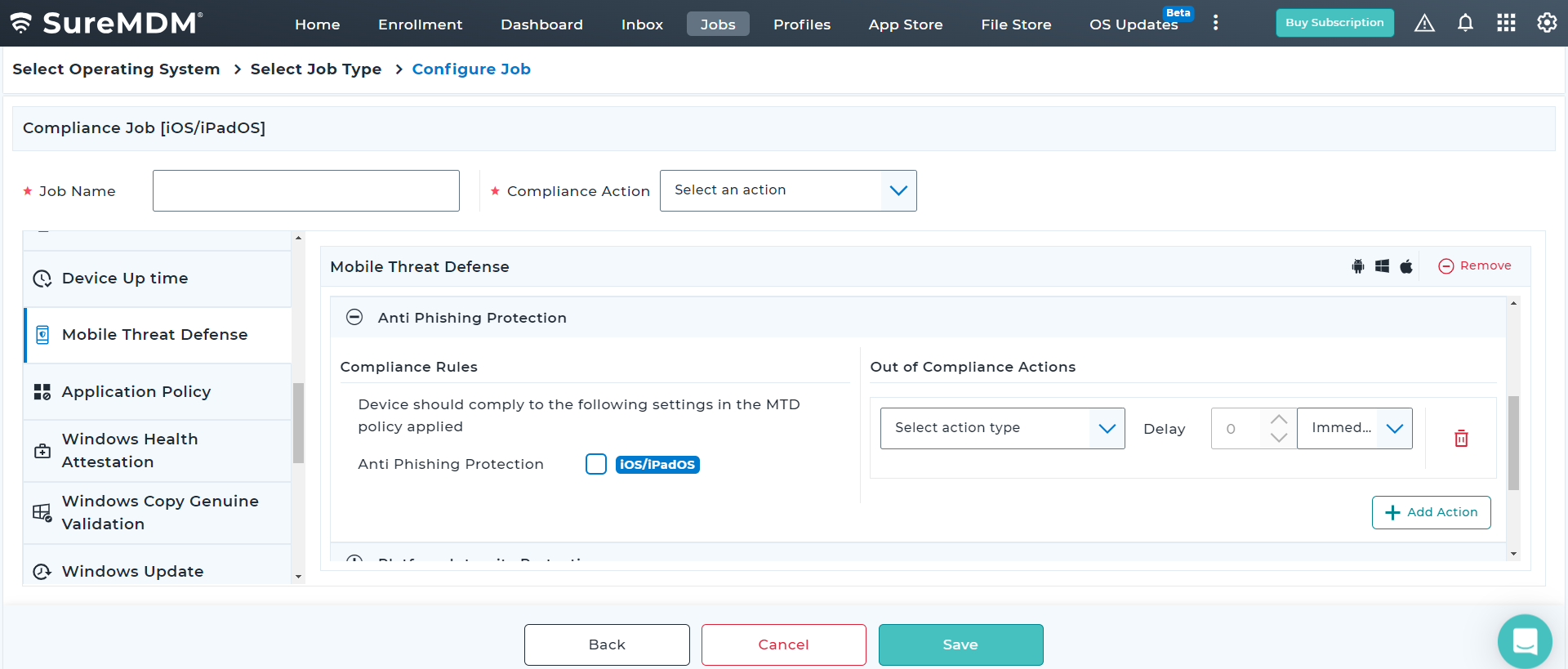
With SureMDM, IT administrators can now configure and push Microsoft Defender Antivirus policies on enrolled devices. They can also create compliance policy for MTD and ensure Antivirus is enabled and up-to-date always for Windows devices.
Threat Vectors that SureMDM MTD Windows Solution Covers

Malware
Malware is a harmful software created by hackers for illegal purposes like eavesdropping and password collection. SureMDM Mobile Threat Defense scans endpoints for threats across all vectors, proactively eliminating detected irregularities.

Malicious Apps
Malicious apps are deceptive, often repackaged with harmful codes. Users accessing third-party app stores risk downloading these threats. SureMDM MTD safeguards enterprise data through app scanning and analysis.

Phishing
Threat actors direct phishing links to targeted recipients through emails. SureMDM MTD employs filters to compare links against an exhaustive list of malicious phishing URLs, notifying users if it finds a match.

System Vulnerabilities
Unpatched OSes or rooted endpoints may become great liabilities within a perimeter-less workplace. SureMDM MTD features monitor various system parameters to identify vulnerabilities on devices.

Man-in-the-Middle Attacks
Unsecured networks are an open invitation to hackers. Threat actors steal information by eavesdropping into a conversation between two parties through a compromised channel/network. SureMDM MTD scans wireless networks for malicious behavior and thereby prevents any Man-in-the-Middle attack.
Key Features
Proactively monitor the security of critical business applications, archived documents, emails, network files, and drives at regular intervals. Choose between quick, full device, custom folder, and Microsoft Defender offline scans to meet different requirements.
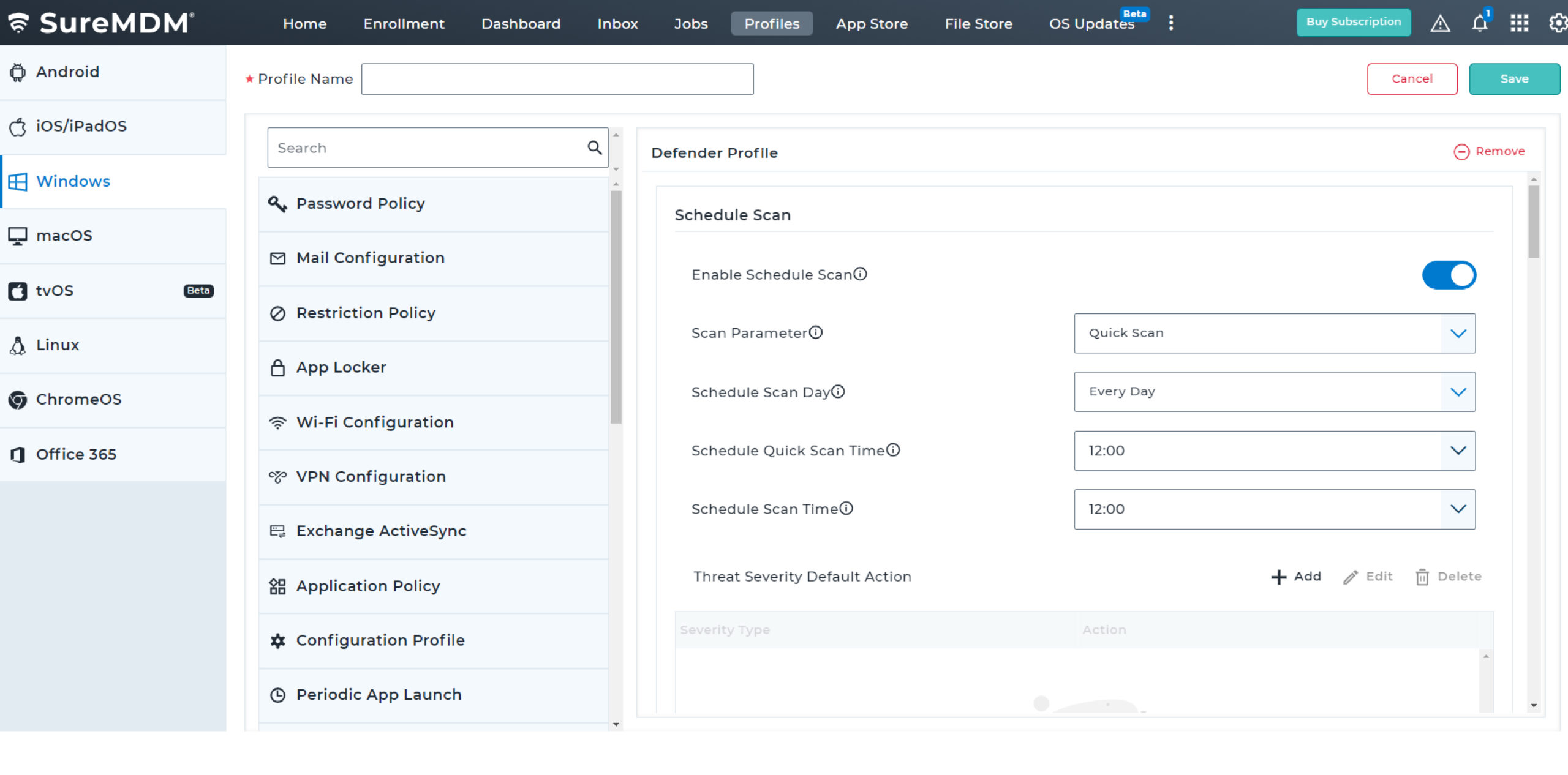
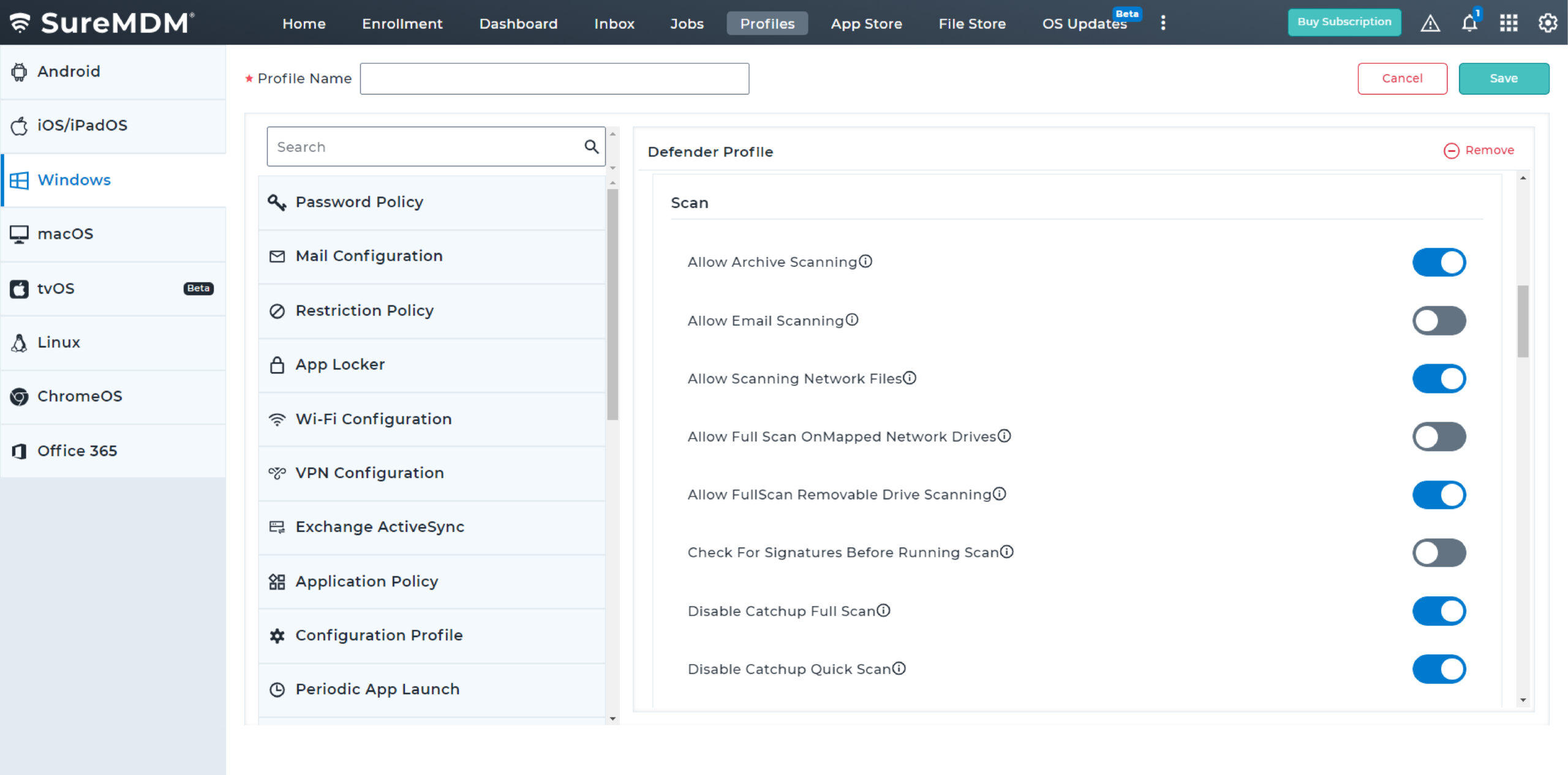
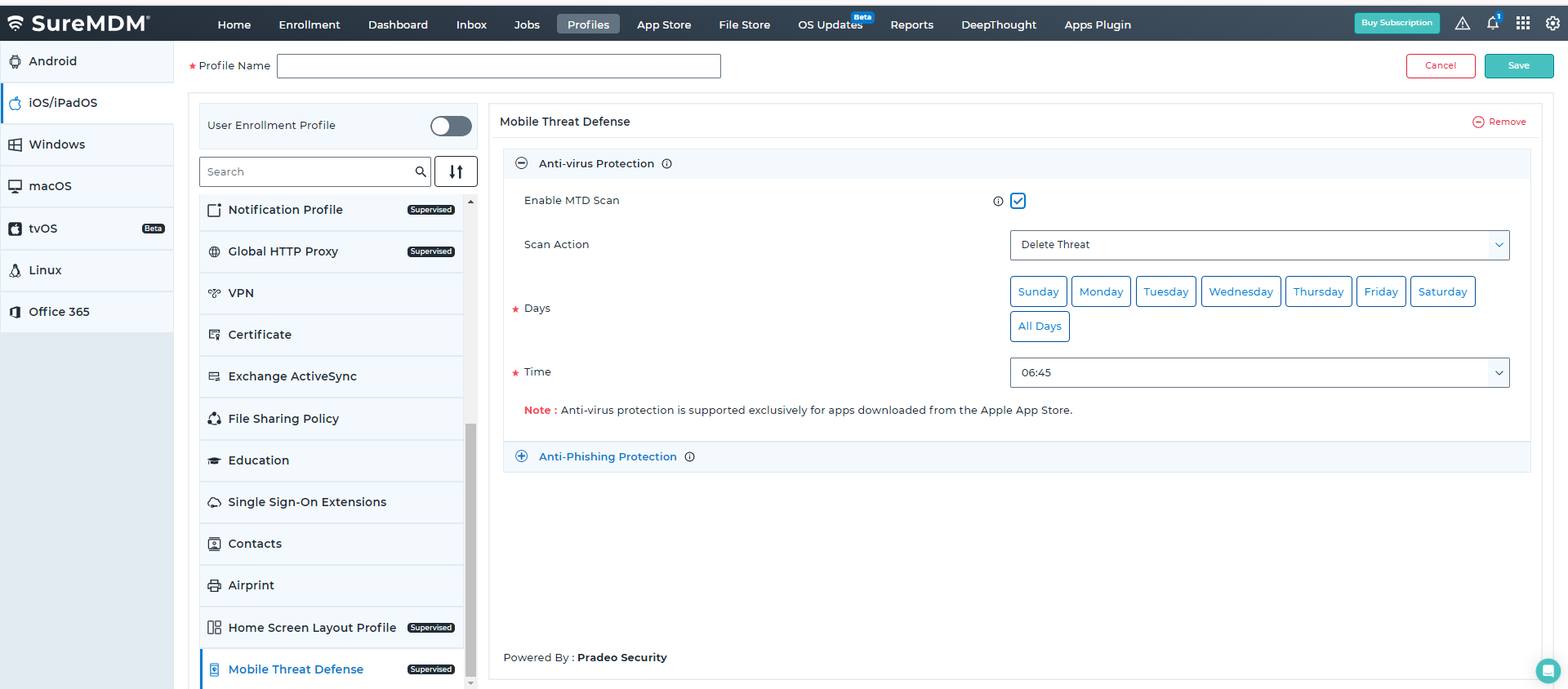
SureMDM has partnered with Pradeo to offer a Mobile Threat Defense (MTD) solution for iOS devices, enabling IT admins to protect and manage a fleet of iOS devices from a unified console.
Threat Vectors that SureMDM MTD iOS Solution Covers

Potentially Harmful Apps
SureMDM Mobile Threat Defense solution actively scans the App Store applications on iOS devices for malware/adware apps, and proactively removes them upon detection.

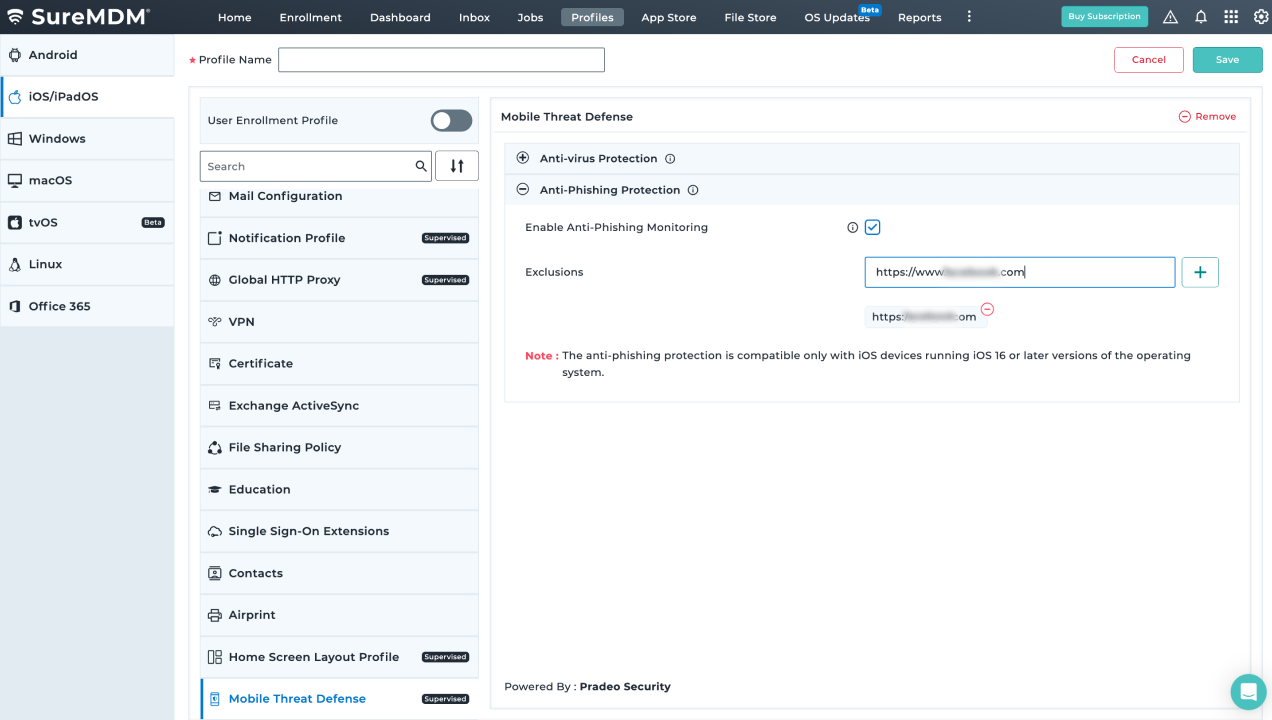
Phishing
Threat actors send malicious links via email to trick recipients into clicking, leading to data leakage. SureMDM MTD protects iOS devices by scanning links and alerting admins of potential threats.
Key Features
Schedule app scans to proactively monitor the critical business applications.
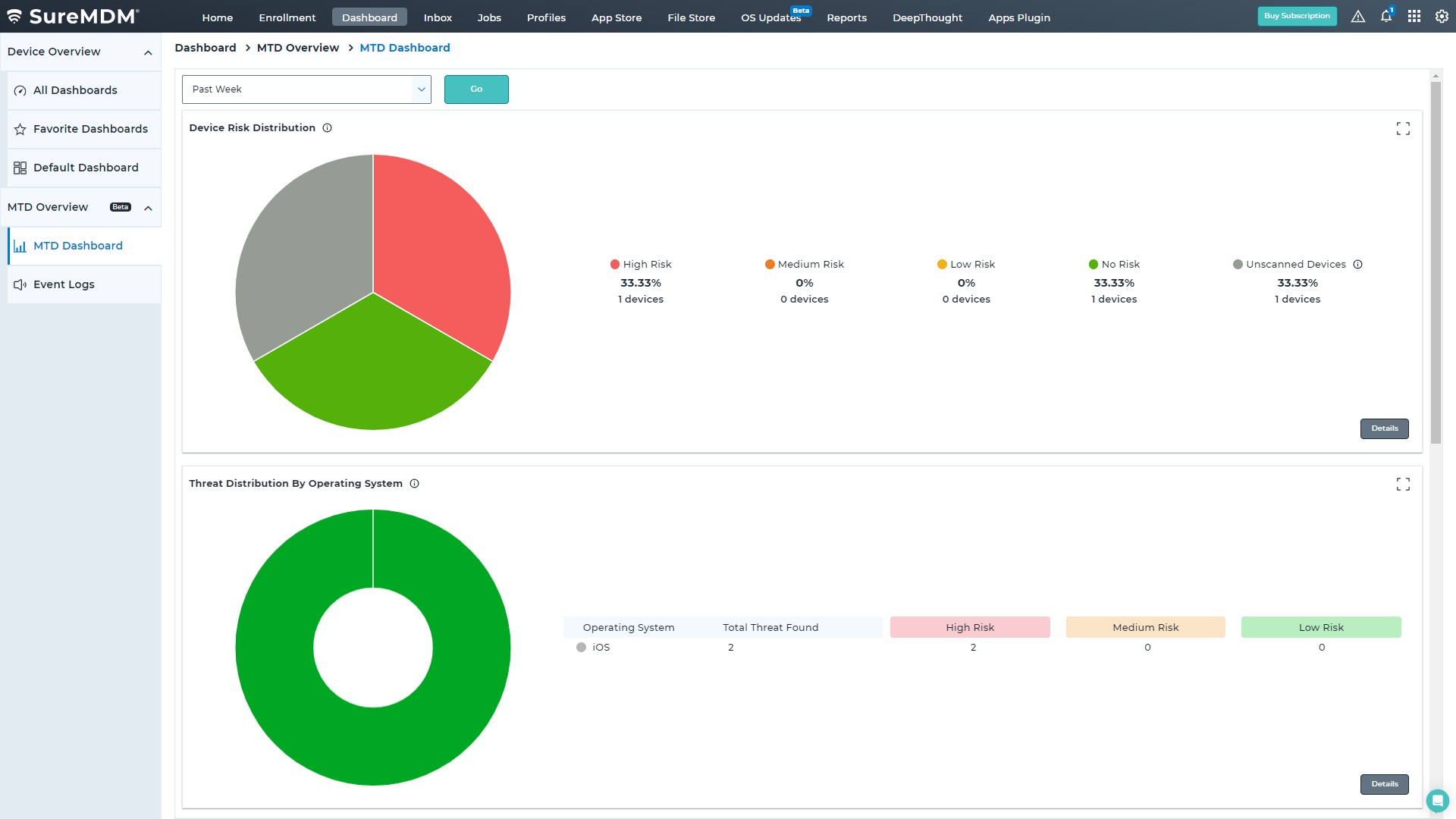
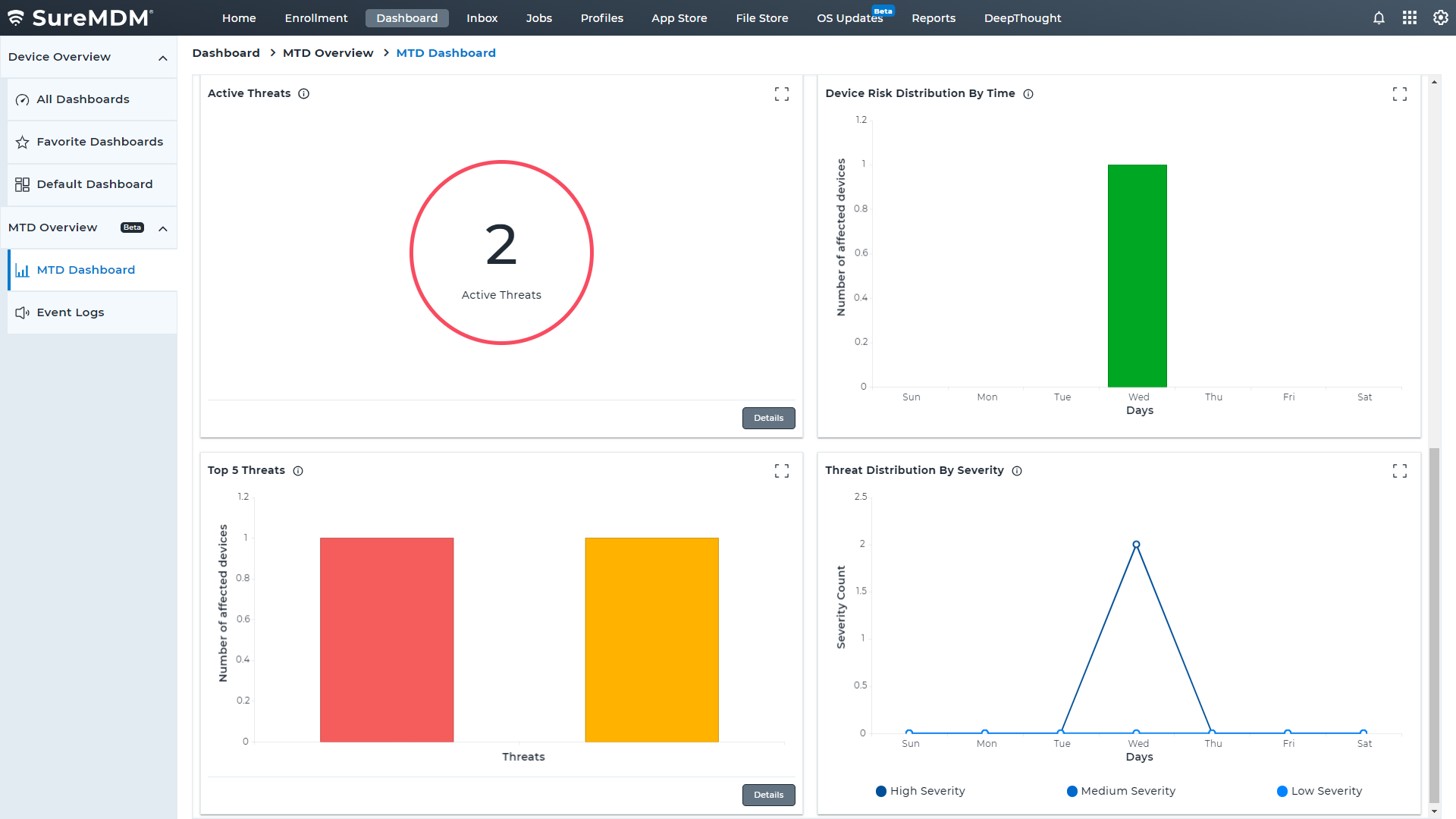
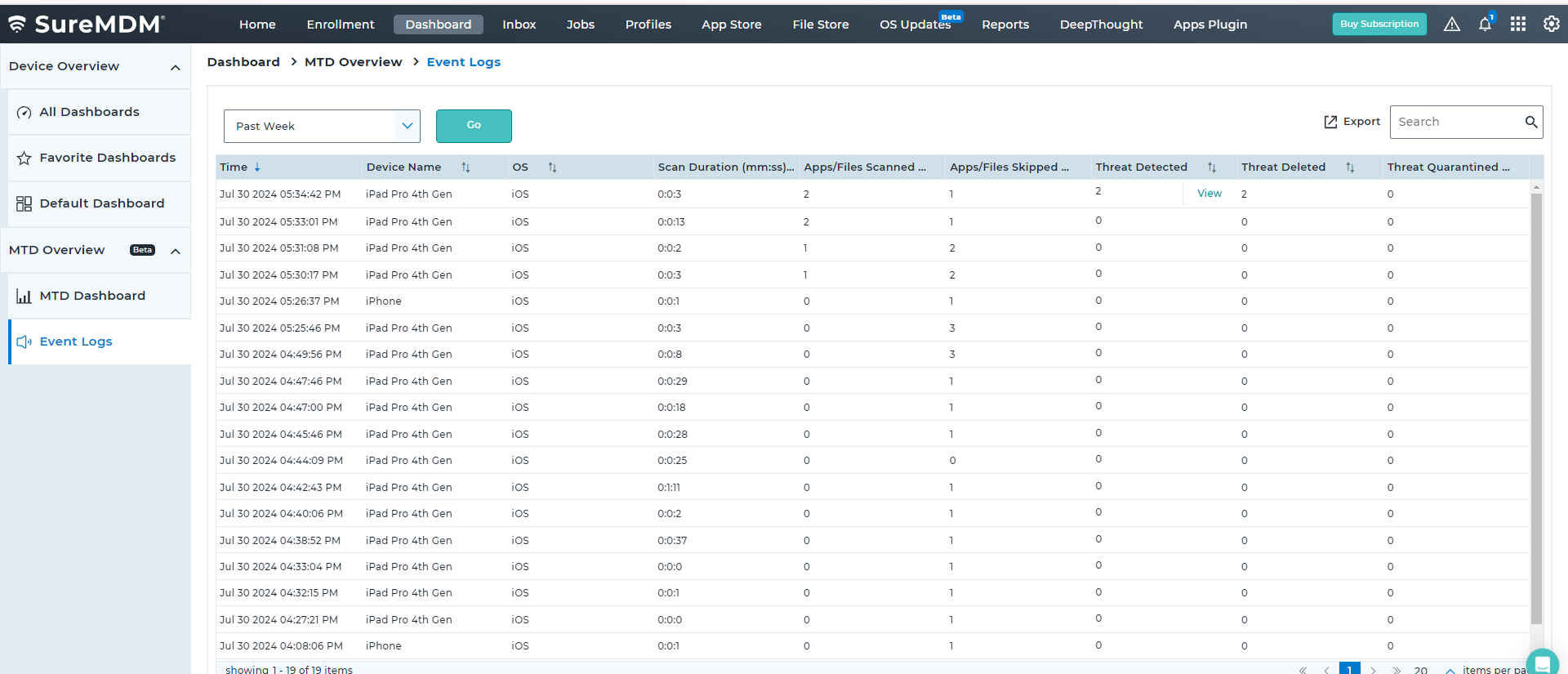
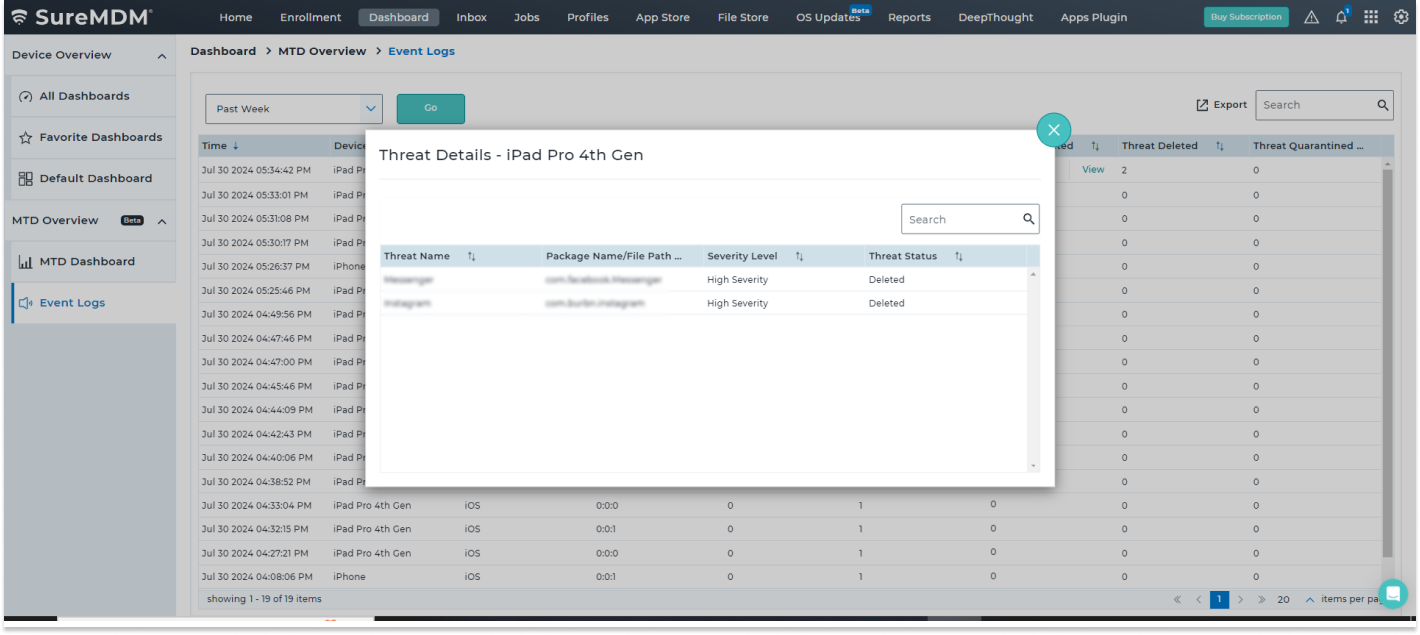
FAQs
How to get started with MTD?
- Android: Download and install the SureDefense app from the Google Play Store or reach out to the 42Gears support team. Once installed and granted all the required permissions, users with active SureMDM licenses should be able to scan their mobile devices against malware and malicious apps. MTD functionality can be activated either by scheduling device(s) scan or a device on-demand.
- Windows: SureMDM uses the default Microsoft Defender Antivirus to scan and protect against cyber threats. Here are the steps to create your Defender Profile.
- iOS: Users can configure MTD using SureMDM agent. They will need active licenses, grant all necessary permissions, and scan their devices against potentially harmful apps and phishing attacks.