Identity Provider Solution
The Key to Secure Digital Access
What is an Identity Provider?
An Identity Provider (IdP) is a system that creates, maintains, and manages digital identity information. Digital identities are unique attributes and credentials that authenticate and authorize individuals in digital environments. These can include usernames, passwords, biometric data, and other identifiers that establish who you are and what you can access in digital systems.
IdPs (Identity Provider Solutions) serve as the central hub for authentication, enabling Single Sign-On (SSO) and streamlining credential management.
💡Example: When you log into Adobe using your Google account, Google Workspace acts as the identity provider, and Adobe is the service provider.
Any website that requires a login typically relies on an IdP to verify user identities, using methods like passwords or other authentication factors.
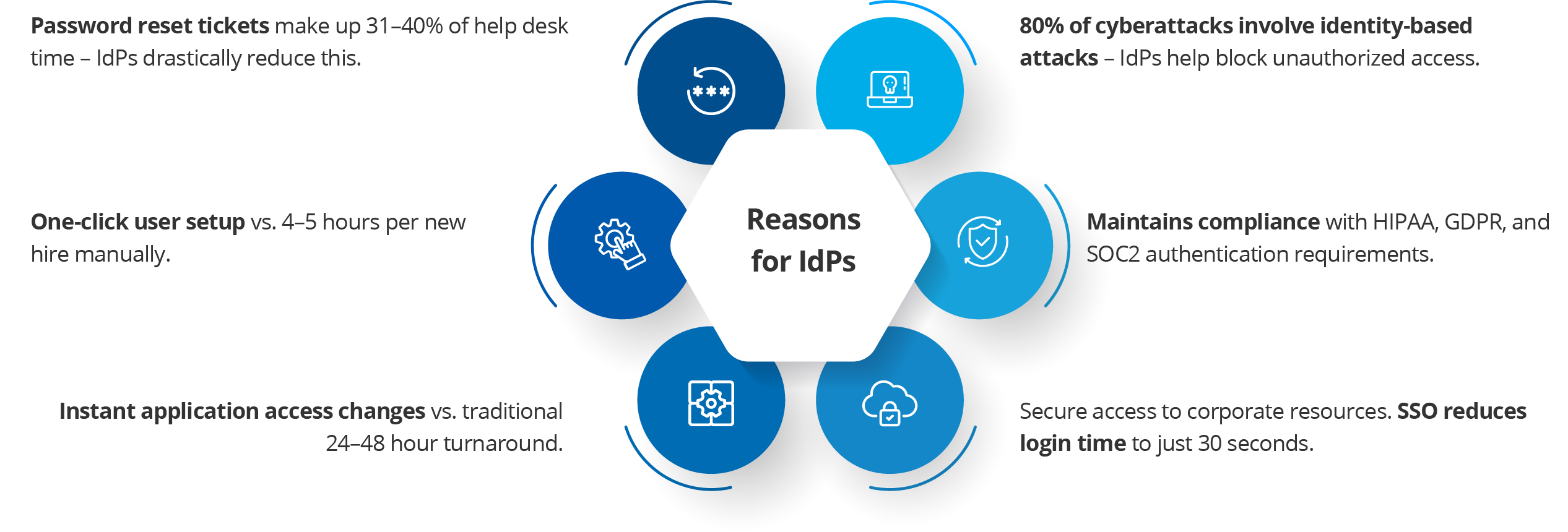
Why are IdPs Necessary?
How do IdPs work?
An IdP workflow involves these key steps:
- User Tries to Access an Application: The user opens an app (e.g., Salesforce, Outlook) that requires login.
- App Redirects to the IdP: The application sends the user to the Identity Provider (e.g., SureIdP, Okta) for authentication.
- User Logs in via IdP: The user enters their credentials (e.g., password, MFA, biometrics) on the IdP login screen.
- IdP Verifies Identity: The IdP checks the credentials and enforces any security policies like device trust or location-based access. IdP Issues a Secure Token (SAML or OIDC): The IdP generates a secure authentication token using a protocol like:
- SAML (Security Assertion Markup Language): Sends an XML-based assertion with the user’s identity and access permissions.
- OIDC (OpenID Connect): Sends a JWT (JSON Web Token) that contains the user’s identity and claims. These tokens act as proof that the user has been verified.
- Token Sent to the Application: The token is passed to the application (called the Service Provider), which validates it using pre-shared trust settings.
- Access Granted: The application grants access to the user based on their identity and roles defined in the token.
Benefits of an IDP

Enhanced Security
- Centralized authentication control
- Reduced risk of credential theft
- Comprehensive audit trails

Improved User Experience
- Single set of credentials for multiple applications
- Faster access to resources
- Reduced password fatigue

Operational Efficiency
- Lower IT support costs
- Simplified user management
- Automated access provisioning
The Impact of IdPs: A Side-by-Side Comparison
| Feature/Scenario | Without IdP | With IdP |
| Authentication | Multiple logins per user | Single Sign-On (SSO) across systems |
| User Provisioning | Manual setup (4-5 hours) | One-click provisioning |
| Security Risk | High (weak passwords, reused credentials) | Lower (enforced policies, multifactor auth) |
| MFA (Multifactor Authentication) | Not enforced, inconsistent usage | Built-in, policy-driven MFA |
| Device Awareness | No context on device compliance | Access granted only to compliant devices |
| Access Management | Delayed (24-48 hrs for changes) | Instant access updates |
| Help Desk Load | 30-40% time spent on password issues | Reduced ticket volume |
| Audit and Compliance | Scattered logs, harder to track | Centralized logs, better compliance reporting |
| User Experience | Frustrating, inconsistent login flows | Seamless, unified access |
Introducing SureIdP
SureIdP is a modern identity and access management solution that integrates authentication with device compliance to enhance enterprise security. It supports Zero Trust principles by continuously verifying both users and their devices before granting access.
This ensures that only trusted, compliant endpoints can access resources, helping organizations reduce security risks, simplify onboarding, and streamline access across applications and systems.

FAQs
What is an Identity Provider (IdP)?
What is an example of an identity provider?
What is identity provider in IAM?
Why use an identity provider?
How do IdPs work?
- Request: The user is requested to enter some form of identity, such as a username and password or biometric authentication.
- Verification: The IdP checks to determine if the user has access, and what they have access to.
- Unlocking: The user is given access to the specific resources to which they are authorized.