Achieving Zero Trust Security: A Complete Overview
out 23, 2025 | Nareddy Saivikas Reddy
What is Zero Trust Architecture?
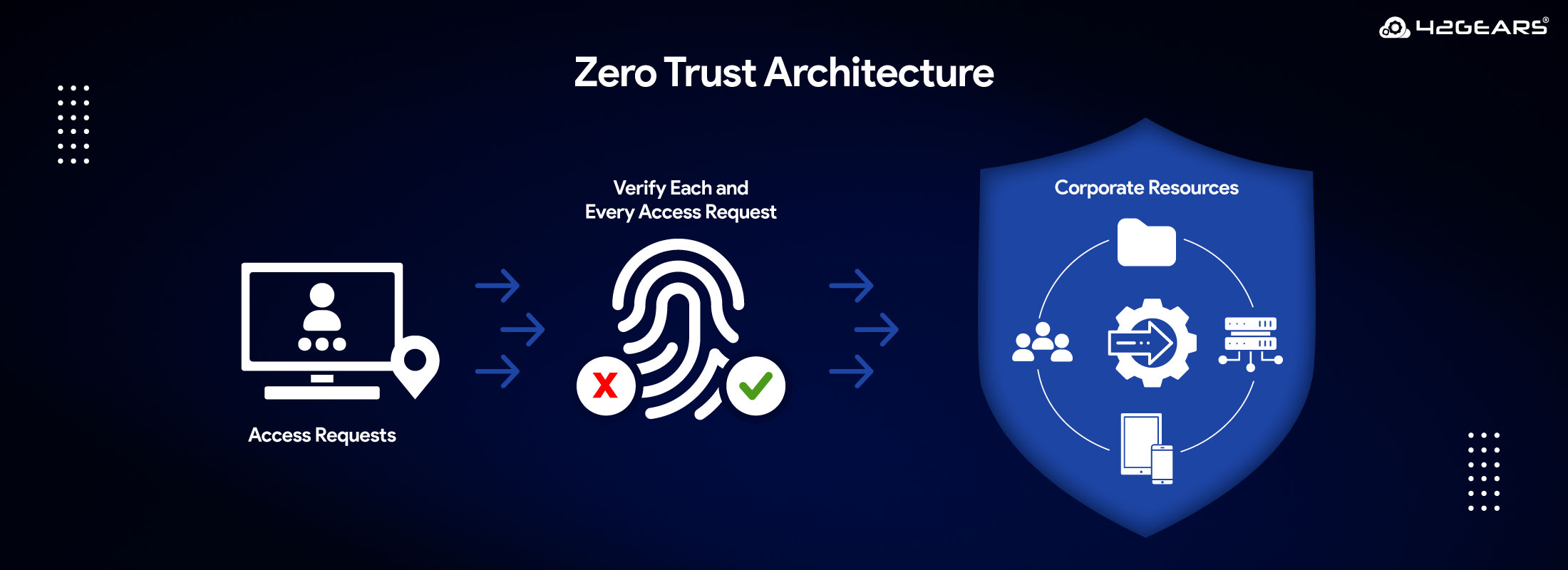
Zero Trust Architecture (ZTA) is a modern security framework that works on the principle “Never Trust, Always Verify”. Zero Trust Architecture challenges the traditional notion of implicit trust within network environments. Zero Trust model assumes that no user, device, or application should be trusted by default — even if it's inside the network perimeter.
Before we move further on to the Zero Trust Architecture, let us understand the history behind it.
🕰️ Evolution of Zero Trust Architecture
Traditional models always assume that threats would come only from external sources. But as cyberattacks became more sophisticated and insider threats more prevalent, these legacy models began to show their limitations. Once an attacker breached the perimeter, they often had unrestricted lateral movement across internal systems.
Zero Trust Architecture (ZTA) originated as a response to these legacy security model gaps that failed to protect against lateral movement and insider threats. Early implementations focused on strict identity and access controls, but with the rise of cloud-native applications, BYOD, and distributed workforces, the Zero Trust Security Model expanded to incorporate device posture assessments, continuous authentication, and real-time telemetry.
Today, it's a core pillar of enterprise cybersecurity strategy, endorsed by NIST (SP 800-207) and adopted globally across sectors.
Understanding Zero Trust Architecture
To understand more about the Zero Trust Model, we need to first understand the core principles of Zero Trust Architecture:
What are the Core Principles of Zero Trust Architecture?
These principles form the foundation of any Zero Trust Architecture (ZTA):
- Never Trust, Always Verify: Every access request must be authenticated and authorized, regardless of origin—inside or outside the network.
- Assume Breach: Zero Trust assumes breaches are inevitable—threats can come from anywhere. Always monitor, log, and respond to abnormal behavior.
- Least-Privileged Access: Users and devices should be given only the minimum access necessary to perform their tasks, reducing risk exposure.
- Continuous Monitoring: Trust is not a one-time event. ZTA continuously analyzes user and device behavior to detect risks in real time. It dynamically adapts access policies based on changing context and threat levels.
As Zero Trust becomes essential to modern enterprise security, organizations need tools that align with its principles. That’s where SureMDM steps in — bringing Zero Trust to life with built-in solutions.
How SureMDM Supports Zero Trust Architecture (ZTA)?
Starting from its inception, SureMDM has continuously evolved to address the different business challenges across sectors. Today, as security becomes a top priority, SureMDM takes a significant leap forward by expanding its Zero Trust Architecture (ZTA) offerings. With the addition of built-in Zero Trust Network Access (ZTNA) and Zero Trust Identity and Access Management (IAM) solutions. Let’s take a closer look at both features:
1. SureAccess - Built-in Zero Trust Network Access (ZTNA) Solution: SureAccess is a robust Zero Trust Network Access (ZTNA) solution built to strengthen enterprise security and enable secure, policy-driven access to corporate resources. Based on the core principles of Zero Trust Architecture, it enforces strict verification of every user and device—regardless of their location—before allowing access.
Key capabilities include:
- High-performance tunneling
- Split tunneling to reduce network bottlenecks
- DNS-based access control for domain-level policy enforcement
- Per-app VPN for granular traffic segmentation
- Context-aware network access policies based on user, device, and network posture
2. SureIdP - Built-in Zero Trust Identity and Access (IAM) Solution: SureIdP is a native Identity and Access Management (IAM) solution built on Zero Trust principles, offering secure authentication, granular access control, and continuous validation of users and devices based on device posture at every access point to reduce risk and prevent unauthorized access.
Key capabilities include:
- Cross-platform device authentication
- Native OS login integration for seamless sign-in
- Conditional access policies for context-based enforcement
- External identity federation with leading IdPs
🔐 Zero Trust: A Security Baseline, Not a Choice
As the threat landscape continues to evolve, relying on perimeter-based security models is no longer enough. Zero Trust is not just a framework—it’s a fundamental shift in how modern organizations protect their users, data, and infrastructure.
Solutions like SureAccess and SureIdP aren’t just add-ons—they are core enablers of Zero Trust adoption. From verifying every access request to enforcing least-privileged policies and contextual authentication, SureMDM helps you turn Zero Trust principles into actionable security.
Strengthen your security posture with
Zero Trust Architecture (ZTA)
Subscribe for our free newsletter