Obtaining Authentication Certificates Using SCEP
Aug 14, 2018 | 42Gears Team
Extensive use of mobile devices in enterprises raise security concerns such as accessing work emails with unauthorized devices, password theft, accessing of corporate resources from untrusted devices etc. Although password-based authentication may secure corporate devices and networks, it has two key disadvantages:
- Users need to remember passwords for each resource they have access to, resulting in a bad user experience.
- Password based authentications are open to brute-force attacks.
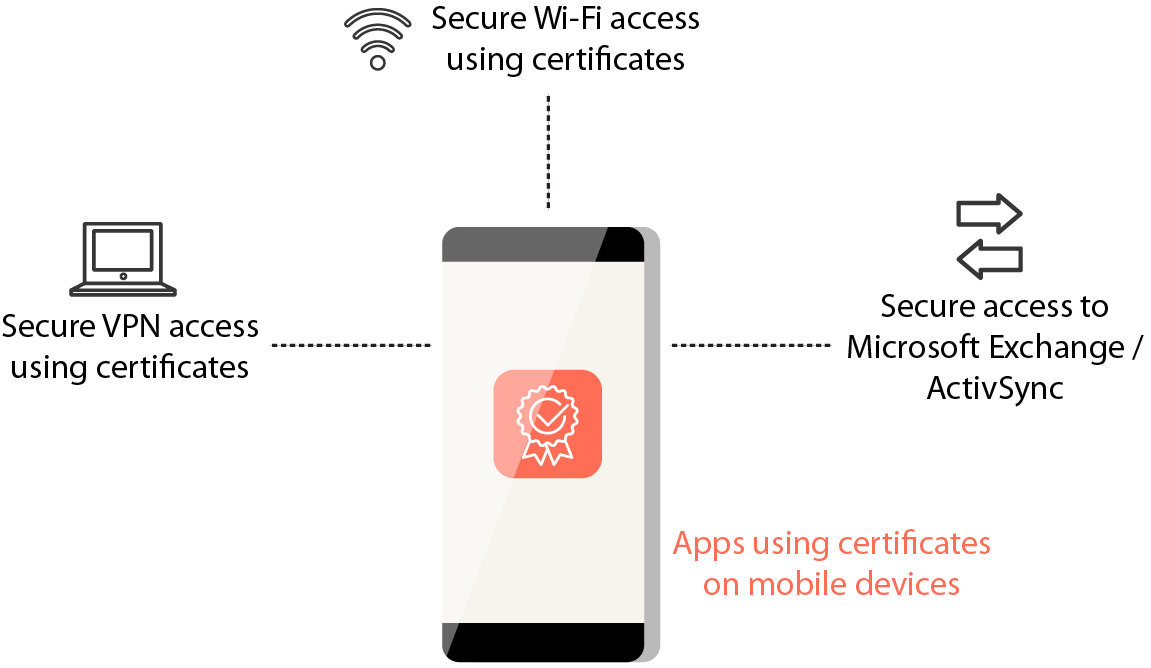
Using digital certificates for enterprise devices ensures authentic use of devices and corporate networks, securing them from external threats. Companies can setup security policies in a manner that, apart from username/password, devices need to have valid certificates installed before they are granted access to enterprise resources such as emails and Wi-Fi network.
Certificates can now be included in an MDM profile in multiple ways for different purposes such as allowing users access to work email or corporate network from only assigned devices.
But these certificates can be leaked or stolen. In order to safeguard against such situations, enterprises must use different certificates for each devices. If a device certificate is stolen, the admin can block or cancel that certificate and issue a new one for that particular device. This will be a better and more secure option than having a single certificate for all enterprise devices.
Certification-Based Authentication (CBA)
CBA ensures simplicity to authenticate enterprise users without their ID and password. Also, certificate management tasks such as issuing, renewing, and revoking can be systematically arranged by CA (Certificate Authority). However, implementing CBA in large scale devices is a big challenge where deployment of certificates and manually enrollment process are complete.
The Simple Certificate Enrollment Protocol (SCEP) simplifies the certificate enrollment process for a large number of devices. Using SCEP, it’s easy to deploy unique certificates on multiple devices without manual intervention.
SCEP Background
SCEP is a protocol designed to provide digital certificates electronically and easily to the network users. It was developed by VeriSign, Inc. for Cisco Systems, Inc., to facilitate network admin to enroll devices for certificates on large scale.
To enroll SCEP with MDM systems, SCEP profiles have to be created and remotely delivered to devices. Once the SCEP profiles are applied, CA (Certificate Authority) issued certificates will get generated and deployed to devices, enabling them to connect to multiple access points such as work mail server, work Wi-Fi network or VPN.
Advantages of using SCEP
- In order to get a certificate for each device, admins input are not required which reduces their workload.
- Users are not required to remember multiple passwords and can alternatively have certificates deployed to their device using SCEP, which can be used for authentication.
- Certificate Based Authentication is inherently more secure than Password Based Authentication and is recommended for enterprises.
SCEP is the convenient and streamlined way to obtain digital certificates on a large scale. For this reason, it’s extensively used with MDM systems for deploying certificates on multiple devices.
42Gears EMM solutions offer SCEP supported deployment. Try 42Gears EMM Solution for free.
Subscribe for our free newsletter