Mobile Identity Management: Securing User Access on Enterprise Devices
Manage identities the smart way—secure, scalable, and simple.
What is Mobile Identity Management ?
Mobile Identity Management is a security approach that ensures only authorized users can access corporate apps, data, and services on mobile devices. It focuses on managing user identities, credentials, and authentication methods across smartphones, tablets, and other mobile endpoints.
Key Features of Mobile Identity Management
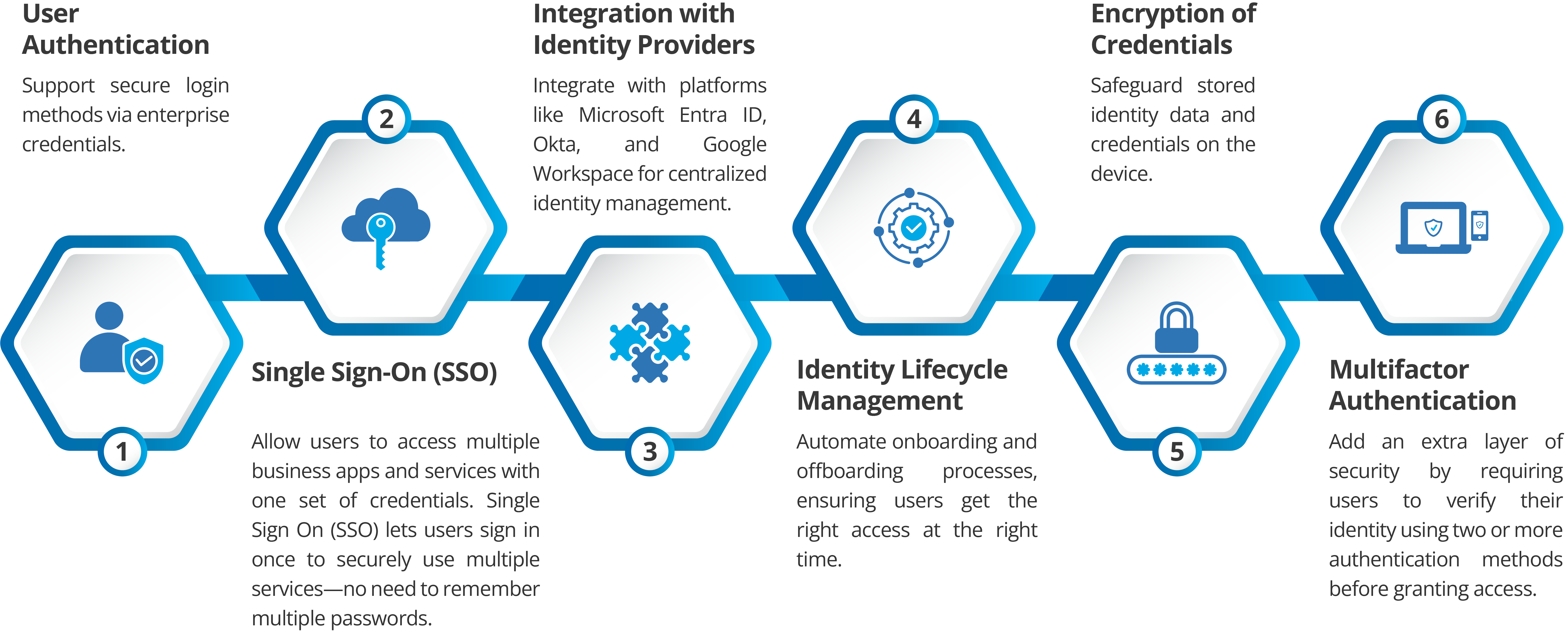
Benefits of Mobile Identity Management
Enhanced Security
Regulatory Compliance
Improved User Experience
Fraud Prevention
Use Cases of Mobile Identity Management

Healthcare
- Challenge
Healthcare professionals frequently use mobile devices to collaborate, communicate, and interact with patient records, telehealth platforms, and clinical apps. However, without robust identity controls on these devices, there's a significant risk of unauthorized identity use, compromised credentials, and exposure of protected health information (PHI). Ensuring secure identity verification on mobile endpoints is critical for maintaining compliance and patient trust. - Solution
Mobile Identity Management secures healthcare staff identities on mobile devices through multifactor authentication, encrypted credentials, and seamless integration with identity providers like Entra ID. Automated identity lifecycle management ensures only current, verified personnel can use clinical apps, reducing risks tied to credential misuse or outdated access. It also supports HIPAA compliance through strong mobile identity controls.
Financial Services
- Challenge
In the financial sector, mobile employees such as sales advisors, auditors, and field officers rely on smartphones and tablets to interact with sensitive data. This increases the risk of identity theft, credential compromise, and regulatory violations of user identities on mobile devices that aren’t properly secured. - Solution
Mobile Identity Management enforces strong user verification through multifactor authentication, encrypted credential storage, and integration with identity providers like Okta or Entra ID or any third-party Identity Providers. Identity lifecycle management ensures only current, authorized staff can access mobile systems—reducing fraud risks without interrupting day-to-day operations.


Retail & E-commerce
- Challenge
Retail employees often use shared mobile devices for tasks like inventory checks, sales, and customer service. In shift-based environments with high turnover, securely managing user identities and ensuring proper authentication is a persistent challenge. - Solution
Mobile Identity Management enables secure, per-user authentication on shared devices, ensuring each employee signs in with their own credentials. Integration with identity providers like Google Workspace streamlines onboarding and offboarding, while encrypted credential storage and MFA reduce the risk of identity misuse in dynamic retail environments.
Mobile Identity Management + Mobile Device Management = End-to-end mobile security
Mobile Identity Management is a key component of Mobile Device Management (MDM) that focuses on verifying and managing user identities on mobile devices. While MDM handles the overall management of the device—such as enforcing security policies, deploying apps, and protecting data—Mobile Identity Management ensures that only authorized users can access corporate resources through features like multi-factor authentication and identity-based controls. Together, they offer a layered security approach that protects both the device and the user, enabling safe and seamless mobile access in today’s flexible work environments.

FAQs
Why is Mobile Identity Management important for businesses?
What is the relationship between Mobile Identity Management and Mobile Device Management?
- MDM manages the device (security settings, app deployment, data protection)
- Mobile Identity Management manages the user identity (authentication, SSO, identity-based control)
Is Mobile Identity Management suitable for BYOD environments?
What are the risks of not using Mobile Identity Management?
What features should you look for in Mobile Identity Management?
How quickly can Mobile Identity Management be deployed across devices?
What is the difference between IAM (Identity and Access Management) and IdM (Identity Management)?
Is Mobile Identity Management scalable for large enterprises?
Protect Your Data on the Go with Mobile Identity Management.



