What is Split Tunnel VPN? Benefits, Risks and How to Secure It with MDM
May 09, 2025 | Rinkalkumar Bhanderi
In the hybrid work era, protecting sensitive data without compromising user experience is critical. That’s where VPNs, and more specifically, Split Tunnel VPNs come into play. But what exactly is a Split Tunnel VPN, how does it work, why should modern businesses consider it and how do they integrate into a Zero Trust framework with Mobile Device Management (MDM).
Let’s break it down.
What is a VPN?
A Virtual Private Network (VPN) is a secure channel between your device and the internet. It encrypts your data, hides your IP address, and prevents unauthorized access to your activities online. Businesses use VPNs to protect sensitive information when employees connect from outside secure office networks.
Traditional VPNs route all network traffic through a secure server, which ensures privacy but can also result in slower internet speeds, especially when streaming or using cloud applications.
What is a Split Tunnel VPN?
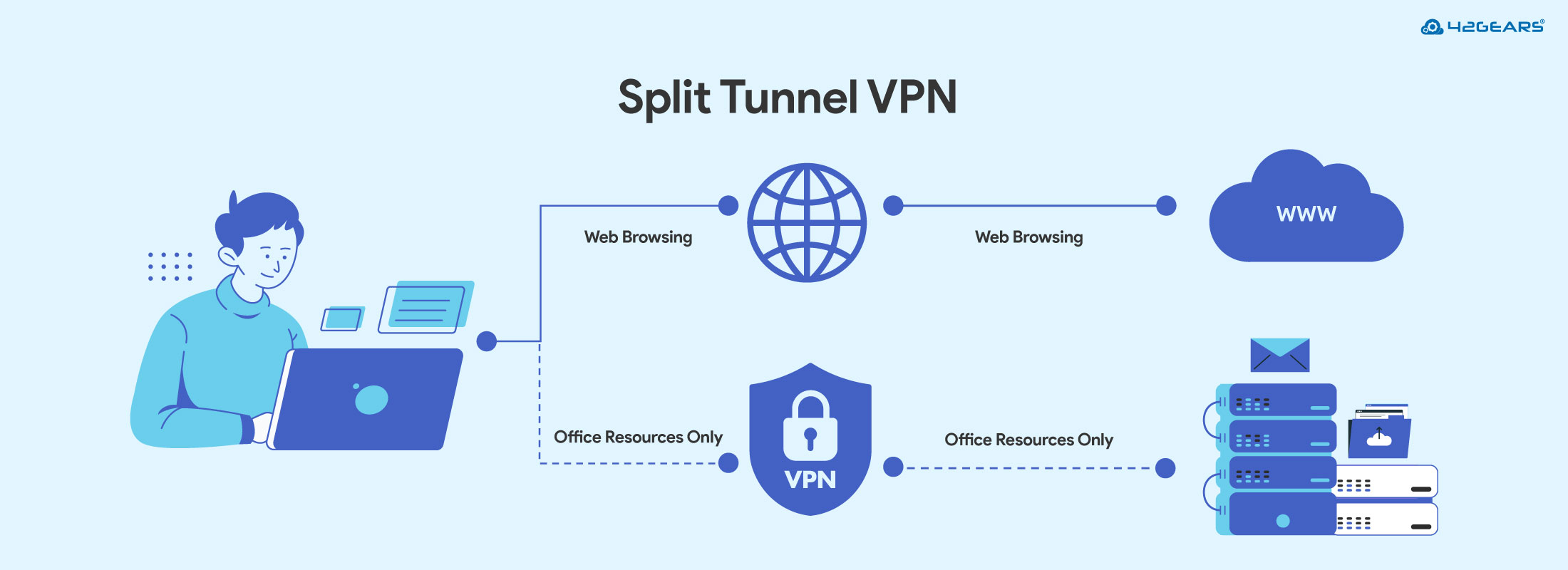
A Split Tunnel VPN allows users to send some traffic through the encrypted VPN tunnel while allowing the rest to access the internet directly.
Here’s how it works:
- Secure Data (e.g., internal apps, sensitive business files) travels through the VPN.
- Public Data (e.g., YouTube, news sites, local services) bypasses the VPN.
This dual-routing approach minimizes unnecessary traffic through corporate VPNs, saving bandwidth and improving performance.
Example Use Case:
An employee working from home accesses confidential HR systems via VPN while using Microsoft Teams or browsing public sites via their local internet.
How Does a Split Tunnel VPN Work?
Split tunneling uses network rules to determine which traffic goes where:
- IP-based rules: Traffic to specific IPs is routed through the VPN.
- Application-based rules: Only selected apps use the VPN tunnel.
- Domain-based rules: Specific websites or domains route through the VPN.
This approach requires careful configuration to ensure sensitive data remains protected while optimizing for speed and resource usage.
Advantages of Split Tunnel VPN
1. Improved Performance
By allowing non-critical traffic to skip the VPN, users experience faster internet speeds for general browsing and streaming.
2. Reduced Bandwidth Usage
Corporate networks aren’t overloaded with high-volume, low-risk traffic like software updates or video calls.
3. Increased Productivity
Users face fewer interruptions, especially when working with cloud-based or resource-intensive tools.
4. Flexible Security Policies
Admins can tailor VPN access based on user roles, locations, and risk levels.
Potential Risks and Mitigation
Despite its benefits, Split Tunnel VPNs can introduce vulnerabilities if not properly managed:
- Data Leakage: Unsanctioned apps may access internal networks indirectly if not configured right.
- Malware Entry Point: Devices can get infected via direct internet access and then pose risks to corporate systems.
- Compliance Issues: Partial tunneling might not meet strict data privacy regulations.
Mitigation Strategies:
- Combine Split Tunnel VPNs with endpoint protection and MDM policies.
- Use Zero Trust Network Access (ZTNA) principles to authenticate and validate users and devices.
Monitor traffic continuously using Network Access Control (NAC) tools.
Zero Trust Access and Split Tunneling: A Strategic Fit
Zero Trust is a cybersecurity model that operates on the principle of "never trust, always verify."
In a Zero Trust framework:
- Every user and device is authenticated.
- Access is granted only to what is necessary.
- Continuous validation ensures no lateral movement within the network.
Split tunneling aligns well with Zero Trust when implemented correctly. It allows secure access to corporate resources while enforcing identity-based controls, microsegmentation, and visibility into user activity. The result? Enhanced user experience without compromising on security.
Role of Mobile Device Management (MDM) in Split Tunnel VPN
Mobile Device Management (MDM) plays a crucial role in the successful deployment of Split Tunnel VPNs. It allows IT teams to enforce policies, monitor devices, and ensure compliance across both corporate and BYOD (Bring Your Own Device) environments.
Benefits of Using MDM with Split Tunnel VPN:
- Policy Enforcement: Define which apps or domains use the VPN.
- Device Posture Assessment: Ensure only secure, updated devices gain tunnel access.
- Remote Management: Lock, wipe, or update devices remotely in case of compromise.
- Compliance Assurance: Track and audit device behavior to meet regulatory standards.
Challenges Without MDM:
- Inconsistent security across devices
- Lack of visibility into traffic or app usage
- Inability to enforce split tunnel rules effectively
- Increased risk of shadow IT or unauthorized app access
How SureAccess by 42Gears Solves All These Challenges?
SureAccess by 42Gears is a purpose-built solution that takes Split Tunnel VPN and Zero Trust to the next level.
Key Features:
✅ Application-Level Tunneling
SureAccess enables tunneling at the application level. Only pre-approved apps are allowed to access corporate resources, blocking everything else by default.
✅ Seamless MDM Integration
Integrated with SureMDM, SureAccess lets IT administrators apply consistent policies, monitor device health, and update configurations remotely.
✅ Zero Trust Enforcement
SureAccess verifies device identity and security posture before granting access, aligning perfectly with Zero Trust principles.
✅ Improved UX Without Compromising Security
Users can work with speed and flexibility while the IT team ensures protection of sensitive assets.
✅ Centralized Visibility & Control
Admins get real-time dashboards, policy enforcement logs, and control over app-level VPN behavior, all from a single console.
Conclusion
As remote and hybrid work continues to grow, organizations must rethink how they secure data without degrading user experience. Split Tunnel VPNs offer a balanced approach, enabling performance and security side by side.
But to unlock their full potential, businesses must combine split tunneling with:
- Zero Trust policies
- Strong MDM frameworks
- Purpose-built tools like SureAccess by 42Gears
By doing so, you ensure that users stay productive, devices stay secure, and data remains protected.
Take charge of your VPN strategy
with SureAccess by 42Gears.
Enable secure, high-speed Split Tunnel VPN access—
built for your mobile workforce
Subscribe for our free newsletter