Introducing Zero Trust Identity & Access Management (IAM) Solution for Modern Enterprises
Jun 17, 2025 | Vaijayanthi Narasimhan
Imagine this: As an IT admin, you’ve set up every firewall, patched every OS, locked down every endpoint...and yet, one misplaced password or login from a rogue device could bring your defenses crashing down.
You’re not alone, and we understand it’s hard to even imagine this scenario.
You will be surprised to know that 80% of breaches today involve stolen or compromised credentials—and that number will only keep growing as we digitalize businesses. In most cases, it’s not some elite hacker brute-forcing their way in. It’s someone logging in with a valid username and password on an unauthorized or non-compliant device.
That’s where traditional Identity Providers (IdPs) fall short. They verify the ‘who’, but not the ‘what’ or ‘where’. And that’s a big issue.
That’s exactly why we built SureIdP—a modern Zero Trust Identity and Access Management Solution, fully integrated into SureMDM, 42Gears’ Unified Endpoint Management Solution.
SureIdP lets you
- Enhance security posture by ensuring that only trusted devices and users can access sensitive corporate data.
- Enforce strict access controls based on user identity, device compliance, location, and more.
- Simplify user & device onboarding and offboarding, reducing administrative overhead for your IT teams.
Key Features of Zero Trust IAM Solution: SureIdP
Built-In Multi-Factor Authentication (MFA)
Did you know that just deploying two-factor authentication can reduce the risk of data breaches by a whopping 99.9%? Now imagine taking that protection even further. With SureIdP, you can enable MFA and add an extra layer of protection against unauthorized access. This ensures that even if credentials are compromised, unauthorized users cannot gain access without the second authentication factor.
Device-Aware Authentication
With SureIdP, you can ensure that access to your systems is granted only when both the user's identity and device compliance are verified. For example, if an employee attempts to log in from an unmanaged or non-compliant device, SureIdP will block access. This way, you can prevent potential security breaches.
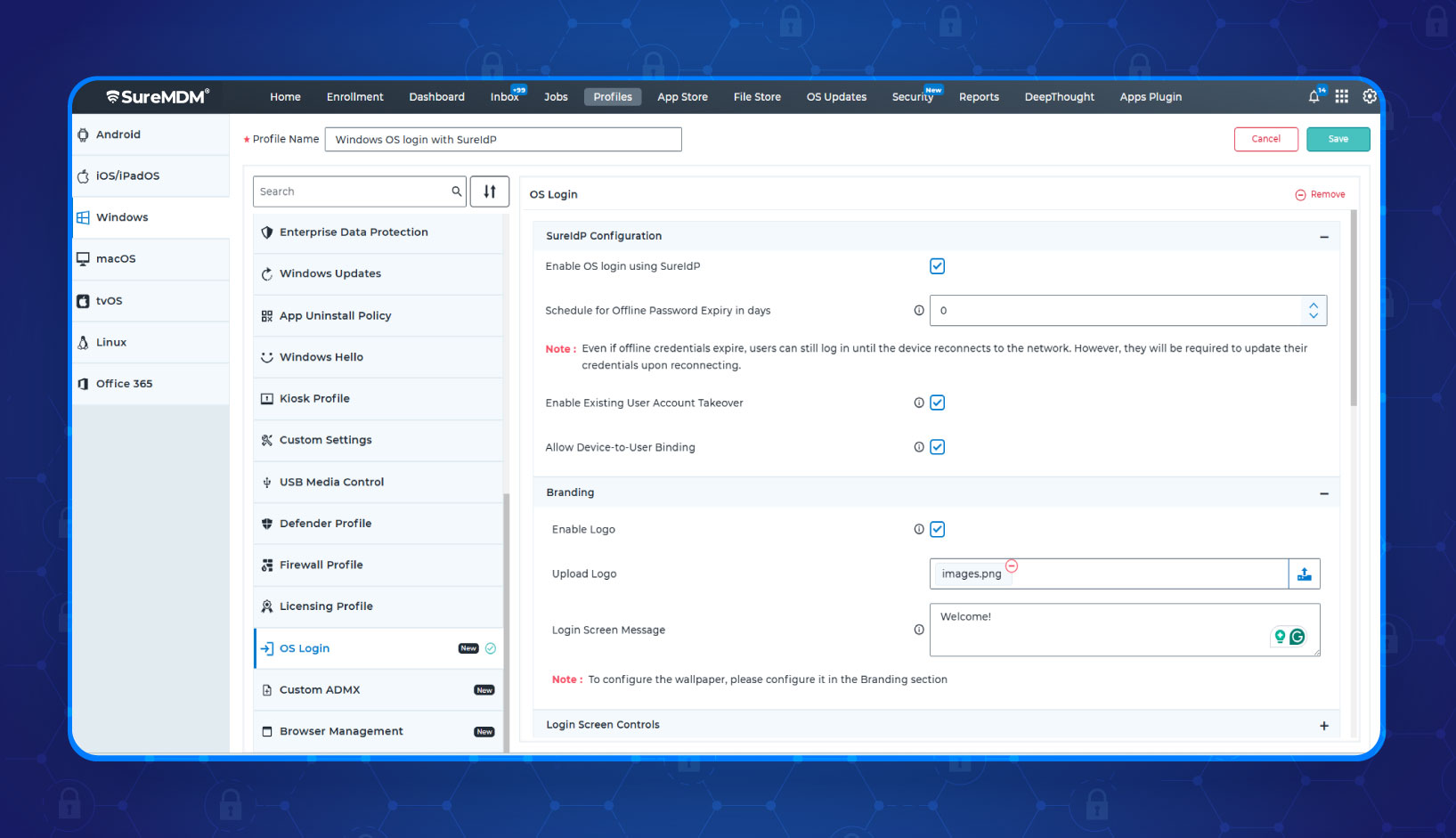
OS Login & Access Control
SureIdP takes device authentication a step further by securing access right at the operating system level. With policy-driven OS login profiles, you can customize the login screen with your organization’s branding and enforce fine-grained controls. Existing user accounts can be taken over while preserving user data. You can also restrict which users can access which devices, hide local accounts, disable shutdown options, and more.
Seamless Single Sign-On (SSO)
SureIdP supports SSO across both cloud-based and on-premises applications. This means your users need not struggle with managing multiple credentials. They can just enjoy a streamlined login experience and access multiple applications with a single set of credentials. The highlight? This works only when they use a compliant device.
Flexible Directory Services
Whether you’re a small company or a large enterprise, you can manage identities the way you want. You can use default domains for simplicity or verify your own custom domain for a more structured user provisioning and better control over access rights.
Contextual Conditional Access
Implement policies that consider the context of access requests, such as location, time, IP Address, and network. For instance, if a login attempt is made from an unusual location or outside of business hours, SureIdP will deny access altogether.
Efficient User Lifecycle Management
Streamline the process of adding and removing users. With SureIdP, you can bulk import users (employees), assign them to groups, and bind them to specific devices. When an employee leaves, their access can be revoked instantly, and their device unbound, ensuring security and compliance.
External Identity Federation
Looking to connect your existing identity systems with minimal hassle? SureIdP integrates well with popular third-party Identity Providers like Google Workspace, Microsoft Entra (Azure AD), and Okta so your users can easily log in using their existing credentials.
What’s more, SureIdP brings in powerful, device-aware authentication to keep things more secure. That means you get the convenience of simplified credential management and a unified login experience, all while maintaining strong security across your organization’s identity ecosystem.
Unified IAM+Device Management Console
Manage users, devices, policies, and applications from a single, intuitive dashboard. This integration eliminates the need to juggle multiple tools, providing a cohesive view of your organization's security posture.
Benefits of SureIdP
- Reduce complexity by managing identities and devices from a unified platform.
- Enhance security through continuous verification and compliance checks.
- Improve operational efficiency with streamlined user management processes.
- Ensure compliance with industry regulations by enforcing strict access controls.
- Lower costs by eliminating the need for separate third-party identity management solutions
How Our Customers Use SureIdP
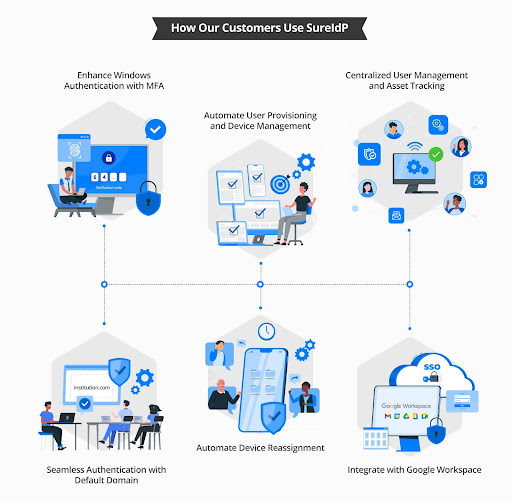
Enhance Windows Authentication with MFA
A global consulting firm secured device access with multi-factor authentication at the Windows login screen. This helped them protect against credential theft without disrupting user workflows.
Automate User Provisioning and Device Management
A financial services company automated their user provisioning and device setup, slashing onboarding time from days to minutes while improving security and IT efficiency.
Centralized User Management and Asset Tracking
A large enterprise solved operational challenges with streamlined user onboarding by linking its centralized user directory directly to OS-level login across managed devices. Devices are auto-assigned hostnames based on user identity, ensuring consistency across the fleet. This integration enhances IT visibility, simplifies asset tracking, and enables better audit and compliance reporting.
Seamless Authentication with Default Domain
An educational institution securely onboarded students without a custom domain. Using the default domain feature, students could authenticate during device enrollment without institutional email IDs. This streamlined BYOD adoption, ensured only authorized access, reduced admin effort, and maintained privacy compliance.
Automate Device Reassignment
A fast-growing company streamlined device handoffs by automating user unbinding and reassignment, reducing transition time and securing sensitive data.
Integrate with Google Workspace
A cloud-native business integrated Google Workspace with SureIdP to enable device-aware Windows logins, preserving single sign-on while boosting endpoint security.
Key Takeaway
We live in a time where identity-related breaches are on the rise, so integrating identity and access management with device management is a must if you want to keep your devices and data secure. In fact, a recent report suggests 60% of organizations have experienced a security incident related to unsecured mobile devices, underscoring the importance of integrating an IAM and MDM solution.
With SureMDM+SureIdP – you get the best of both worlds, zero trust identity and access management combined with powerful device management and compliance, all in one seamless platform. Still on the fence? Zero Trust IAM is no longer a buzzword. Test it out and feel the difference yourself.
Authenticate with confidence. Strengthen
your system’s defense.
Subscribe for our free newsletter








