Conditional Access in Action: How IAM Secures Every Login
aug 29, 2025 | Nareddy Saivikas Reddy
Last Updated: sep 05, 2025
Every login tells a story: who the user is, what is the device used to login, and what they’re trying to access. Understanding that story is the first step toward strong identity security — and that’s where Identity and Access Management (IAM) solutions come in.
So, what’s Conditional Access — and why does it matter now more than ever?
With today’s evolving threats, just ensuring the right people can access the right resources is no longer enough. We need to make sure users are accessing those resources under the right conditions. That’s the role of Conditional Access.
Conditional Access creates a smarter, adaptive security layer — one that evaluates context in real time: Who’s logging in? From where? On what device? And at what time?
Why is Conditional Access in IAM Essential for Businesses Today?
For years, organizations relied on password-based authentication to grant users access to corporate resources. However, in the face of increasingly sophisticated cyber threats, passwords alone no longer offer a strong enough line of defense. Attackers are constantly finding new ways to exploit weak, stolen, or reused credentials — making traditional authentication methods a growing liability.
Let’s take a look at some statistics that highlight why password-based authentication is no longer sufficient — and how it can leave the door wide open for cyberattacks:
- 61% of users1 reuse passwords across accounts.
- Over 15 billion stolen credentials2 are available on the dark web, making brute force and credential-stuffing attacks more effective than ever.
- Over 30% of IT helpdesk calls3 were triggered by password issues—forgotten credentials or account lockouts.
- 81% of hacking-related breaches4 are caused by compromised or weak passwords.
Clearly, passwords can’t stand alone anymore. It’s time for a more intelligent approach.
That’s why we’re excited to introduce the latest features in SureIdP, 42Gears’ built-in Identity and Access Management (IAM) solution — including Conditional Access for Applications and Conditional Access for OS Login. Let’s take a closer look at how they work.
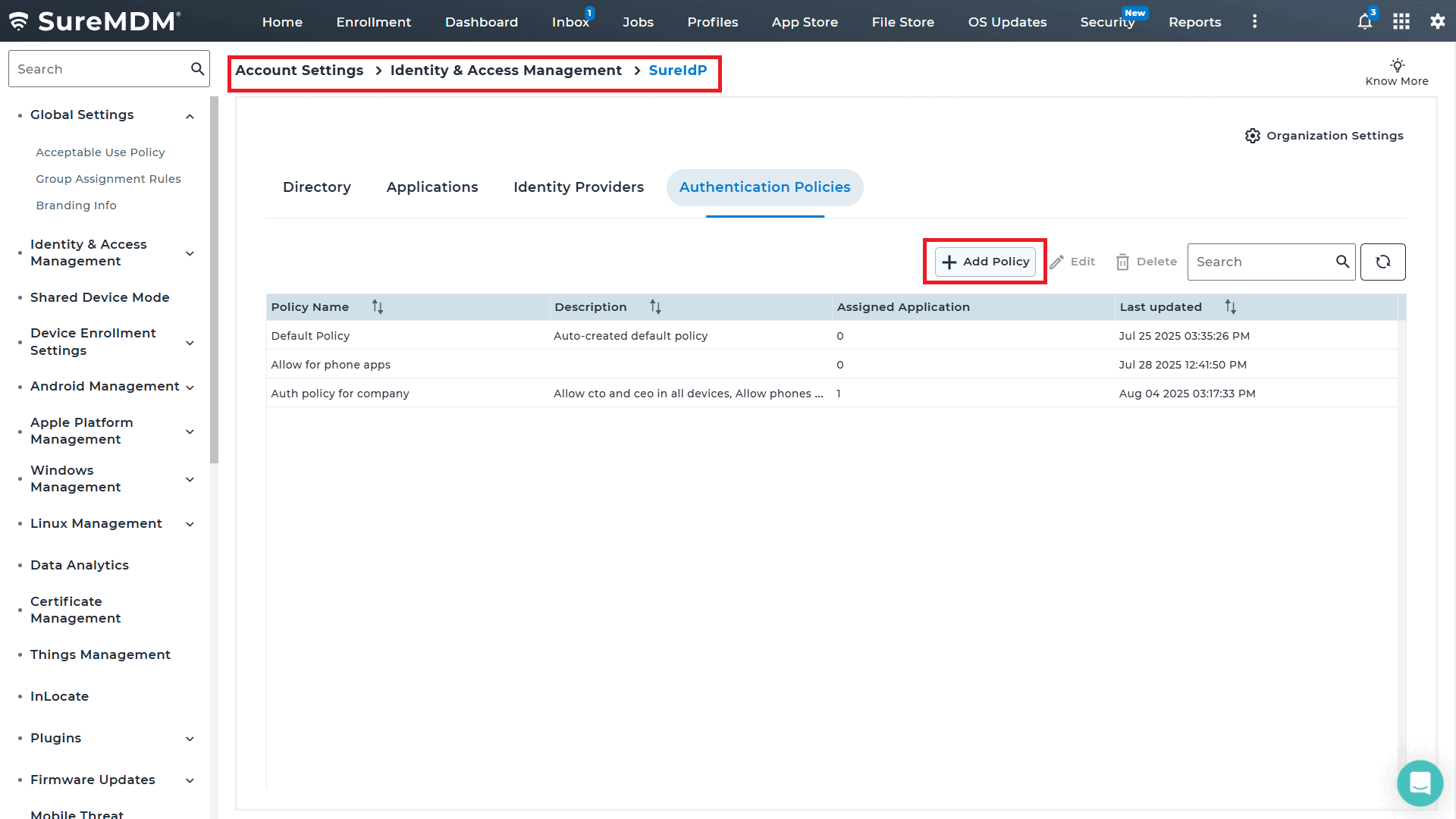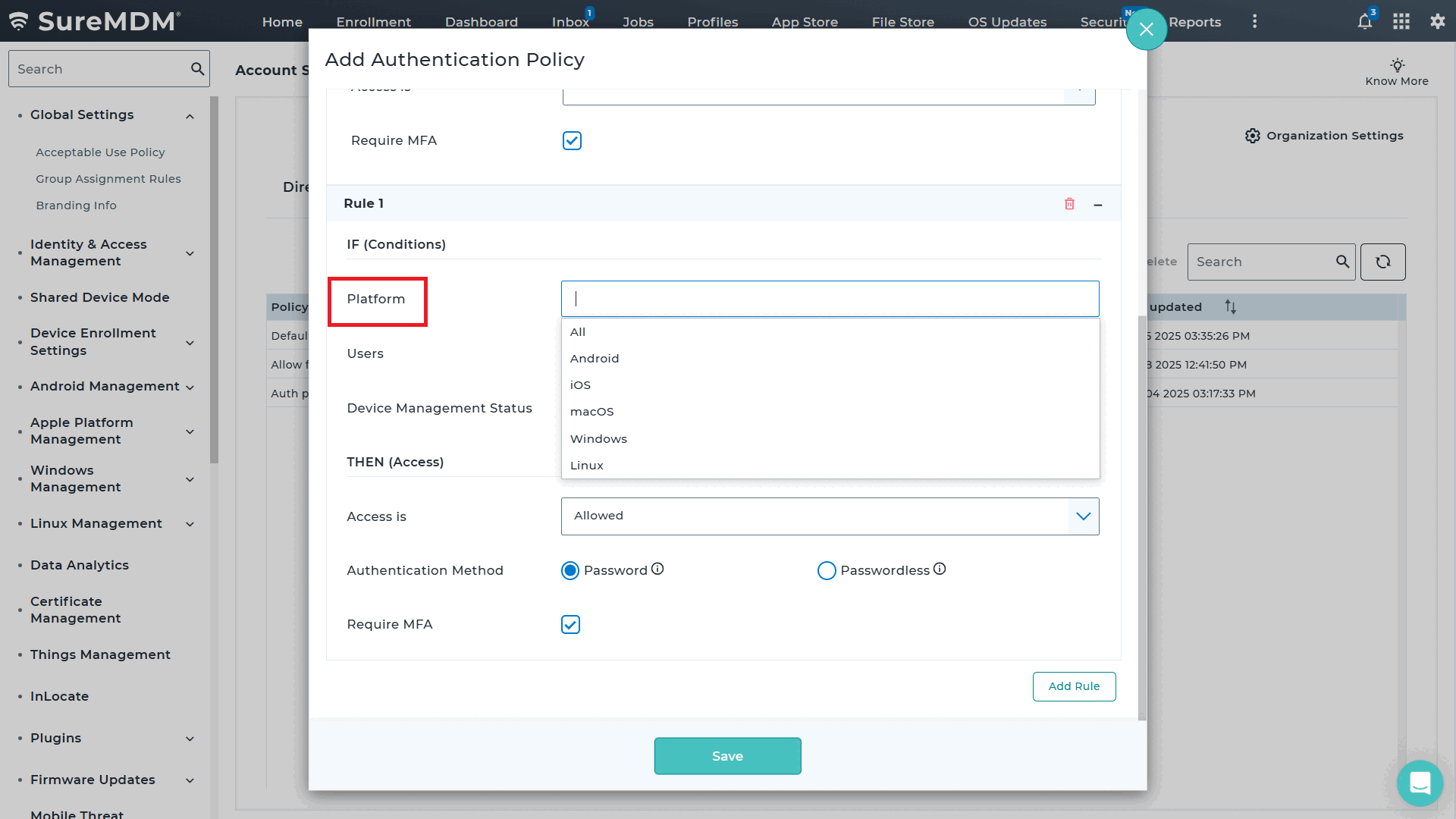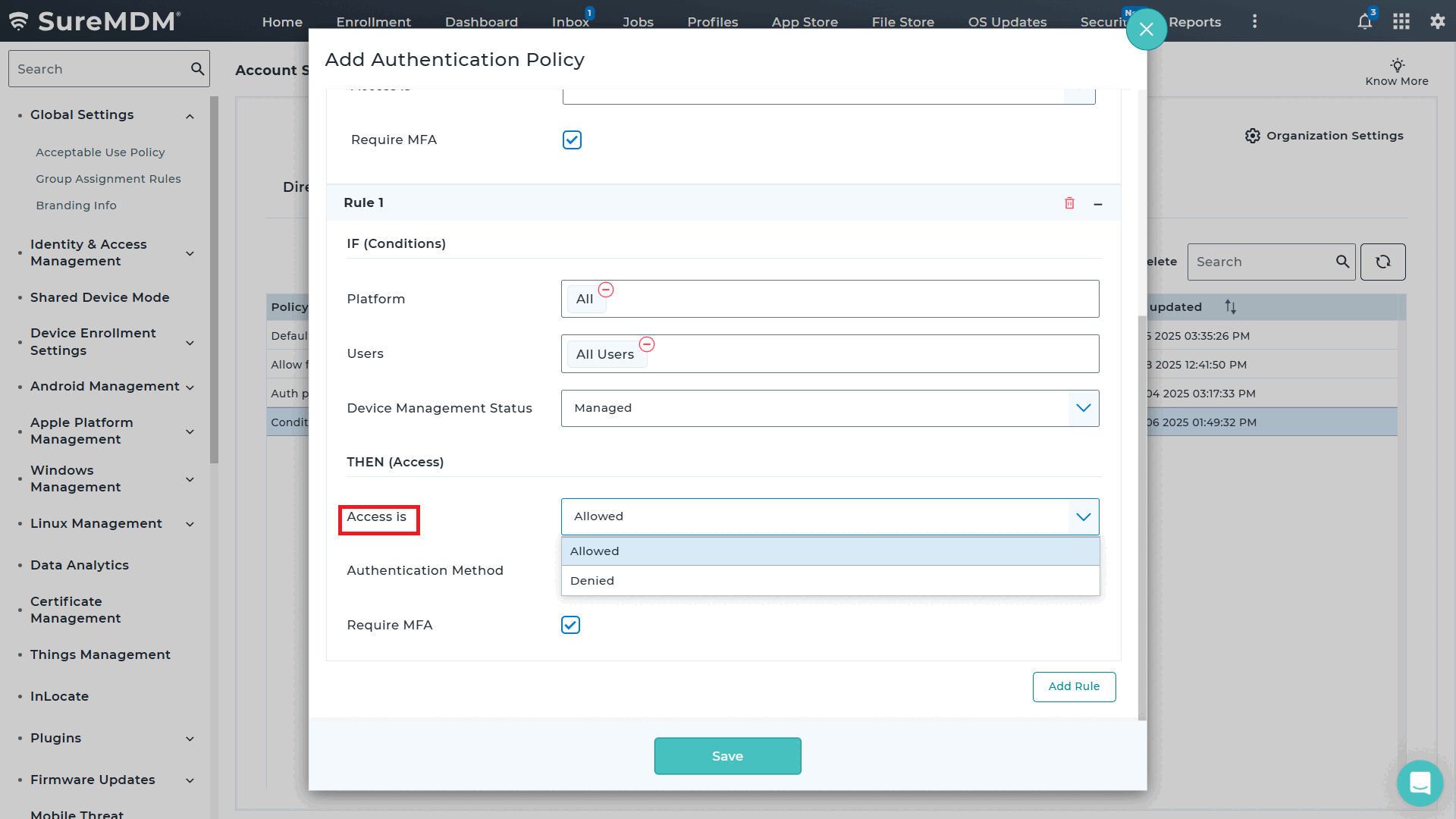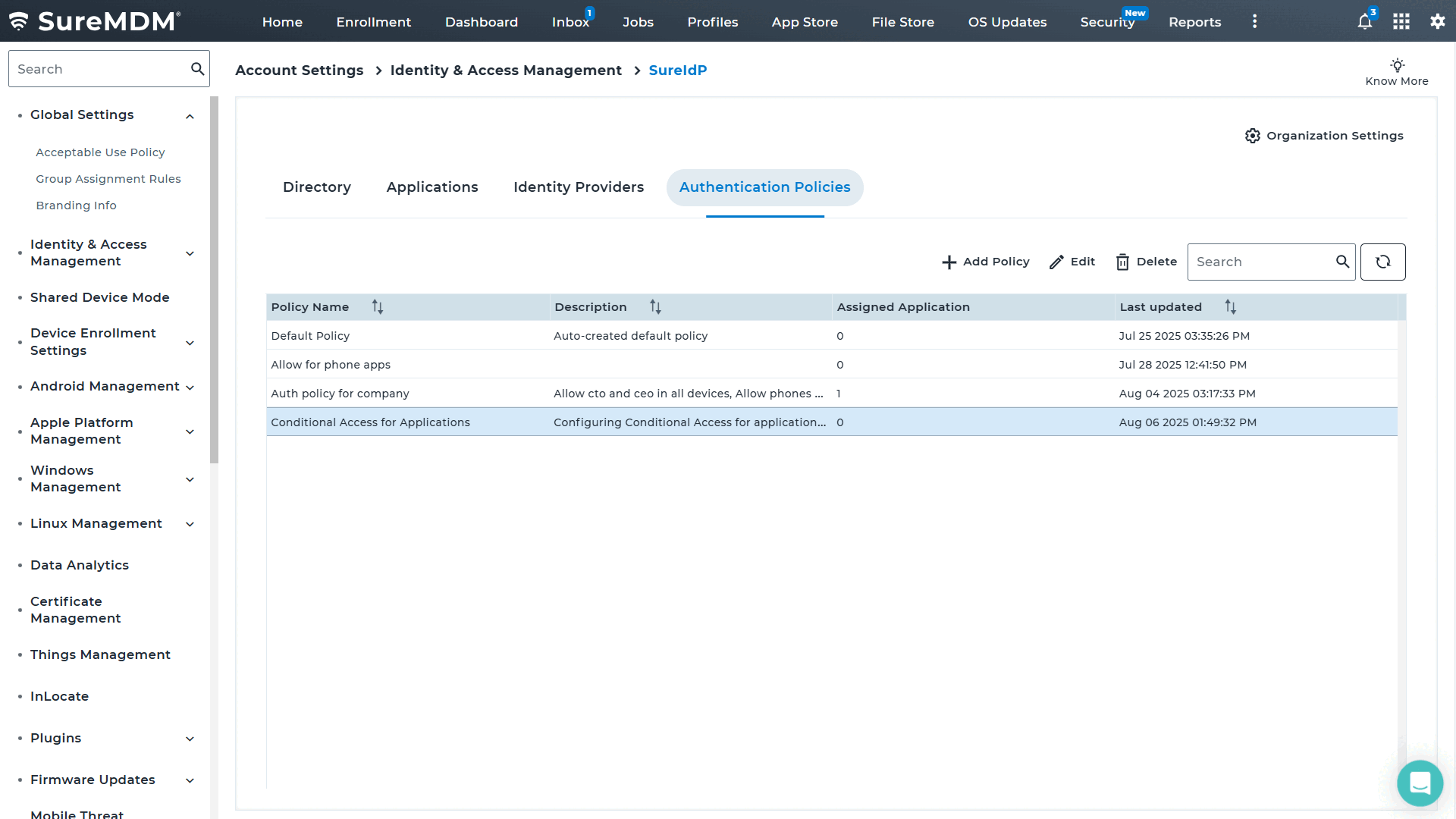
How Conditional Access for Applications Work in SureIdP?
Conditional Access in SureIdP works much like “if-then” statements — if certain conditions are met, then a specific access action is triggered.
Admins can configure policies in SureIdP to allow or restrict access to applications based on several key parameters, making access control both precise and adaptive.
Setting Up Conditional Access for Applications in SureIdP
- Rule-Based Access Control: Start by selecting the platforms — Android, iOS, Windows, or others.
- Targeted User Selection: Apply rules to specific users by entering their usernames or email IDs, or choose “All Users” for universal coverage.
- Device Management Status: Select if the rule applies to Managed, Unmanaged, or All Devices.
- Access Permissions: Allow or deny access based on the configured rule.
- Authentication Method: Choose between Password or Passwordless login, and enable Multi-Factor Authentication (MFA) if needed.
- Adding More Rules: Need more control? Add additional rules (Rule 2, Rule 3, etc.) to handle different scenarios.
- Default Access Behavior: Set what happens when no rules match — allow or deny, with a default auth method.
Learn more about how to configure Conditional Access Policies for applications in SureIdP.
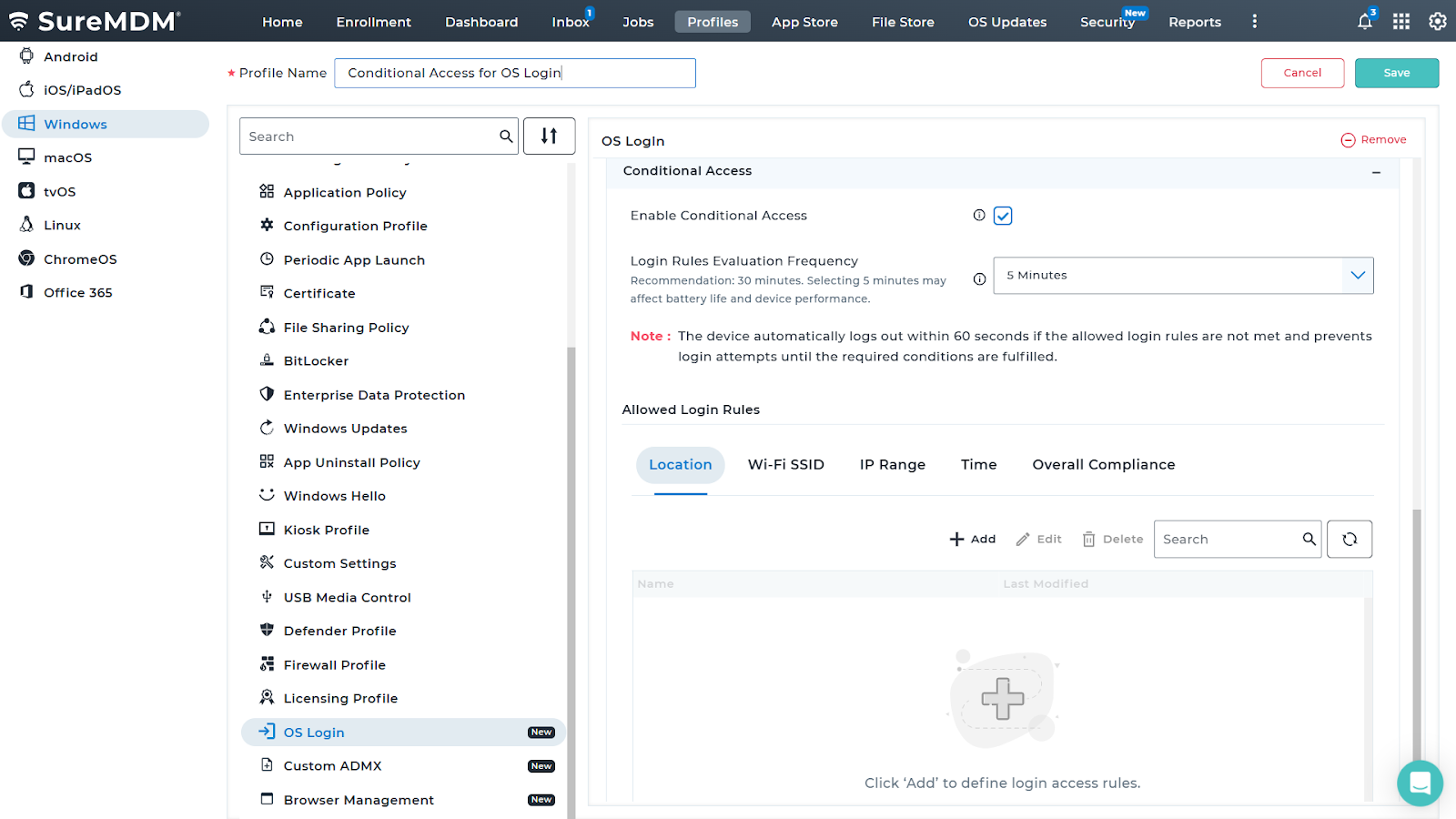
How Conditional Access for OS Login Works in SureIdP?
Admins can configure Conditional Access policies for OS login to control login access to devices based on predefined rules. If a device fails to meet the specified conditions — like location, network, or time — it will auto-logout within 60 seconds and block further login attempts until compliance is restored.
Setting Up Conditional Access for OS Login in SureIdP
- Enable Conditional Access: Start by toggling this setting ON to begin defining login control rules for your devices.
- Evaluation Frequency: Set how often SureIdP should check if the device still meets the login conditions. Recommended value: every 30 minutes (can be adjusted as needed).
- Add Login Rules: Define specific conditions under these tabs to control when and how users can log in:
- 📍 Location:
Allow login only within defined geofenced areas using the map interface. - 📶 Wi-Fi SSID:
Restrict login to trusted networks by specifying allowed SSIDs. - 🌐 IP Range:
Permit access only from selected IP address ranges (e.g., corporate networks). - ⏰ Time:
Limit login access to specific time windows or days of the week. - ✅ Overall Compliance:
Enforce login only if the device is fully compliant with SureMDM policies (e.g., security settings, app compliance, etc.).
- 📍 Location:
🔄You can add multiple entries for each rule type to cover different scenarios.
- Save Profile: Once all rules are configured, click Save.
- Apply to Devices: Navigate to the Home tab, select your Windows, macOS, or Linux devices (or groups), and apply the created profile to enforce Conditional Access for OS Login.
Learn more about how to configure Conditional Access Policies for OS login in SureIdP.
How SureIdP Empowers IT Admins with Smarter Access Control
Meet James, an IT admin at a mid-sized tech firm. His day starts with a notification from SureIdP: a login attempt was blocked on an unmanaged Windows device outside approved office hours and location. Thanks to Conditional Access for OS login, the device was auto-logged out, preventing a potential security incident.
Next, he reviews application access policies. A contractor is joining for a short-term project, so James sets up a new rule in Conditional Access for applications — access to internal dev tools is allowed, but only from managed Android devices, with MFA enabled. The rule takes just minutes to configure and goes live instantly.
Later in the day, a developer tries logging in from the office laptop over public Wi-Fi. SureIdP blocks access due to a login attempt from an unauthorized network. James breathes easy — the system worked exactly as intended.
With SureIdP, James no longer plays catch-up. Access control is proactive, automated, and tailored to every user scenario — across devices and applications.
✅ Benefits of Conditional Access in SureIdP
- Context-aware control based on user, device, and device management status.
- Stronger security by enforcing policies in real time.
- Reduced attack surface by blocking risky access attempts.
- Improved user experience with smart, adaptive access.
- Granular policy enforcement for precise access control.
- Support for MFA and passwordless for enhanced authentication.
- Compliance requirements are met with clear, auditable rules.
Summing Up Conditional Access in SureIdP
Organizations can no longer rely solely on traditional authentication methods like passwords. Ensuring secure access requires a more dynamic, context-aware approach — and that’s exactly what Conditional Access in SureIdP delivers.
Whether it’s controlling access to business-critical applications or securing OS logins based on device, location, time, or compliance status, SureIdP empowers IT admins with the tools to enforce smarter, automated security policies.
Statistics:
- TechRadar and OnePulse
- Okta
- Help Desk Institute (HDI)
- Verizon
Smarter Identity Decisions Start
with the Right Conditions.
Subscribe for our free newsletter


